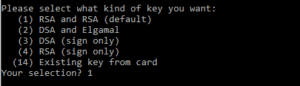
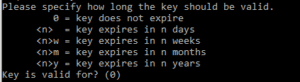
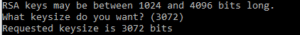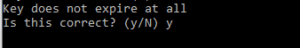In this discussion whiteboard, let us understand what is PKI? What are several components involved in Public Key Infrastructure (PKI)? What are the important skill set required for a candidate to become PKI admin? Are there any specific trainings to undergo for becoming PKI admin? We will discuss these points at high level in this blog article. Let’s get into the topic:
There is a day-by-day increase in the demand for cybersecurity services with the rising penetration of various mobile and wireless devices. The enhancement in mobile and internet infrastructure and advancements in the technology across the globe are propelling the adoption of smart devices across enterprises and consumers. At the same time, enterprises are rapidly embracing cloud platforms and other networking technologies. Because of these advancements, companies are becoming more vulnerable to various cyber-attacks.
In 2017, cyber-attacks on mobile devices increased by over 40% with an average of over 1.2 million attacks per month. Hence, cyber security modules such as cryptography, Data Loss Prevention became more and more critical for the end-users and organizations dealing with sensitive data. The global cybersecurity market is set to grow from its market value of more than $120 billion in 2019 to over $300 billion by 2024. The cybersecurity market is propelled by the increasing need among enterprises to minimize security risks.
All these factors combined contributed to the growth in demand for cybersecurity especially key technologies like PKI – Public Key Infrastructure. With the increase in demand for PKI there is a high requirement in the cyber market for job roles such as PKI admin. In this article we will be focusing on the important skills and trainings that one has to undergo to become PKI admin. Before jumping into the main topic, let us first understand the basics of what is PKI?
What is Public Key Infrastructure – PKI?
The Public Key Infrastructure (PKI) is the set of hardware, software, policies, processes, and procedures required to create, manage, distribute, use, store, and revoke digital certificates and public-keys. PKI or Public Key Infrastructure is cyber security technology framework which protects the client – server communications. Certificates are used for authenticating the communication between client and server. PKI also uses X.509 certificates and Public keys for providing end-to-end encryption.
In this way, both server and client can ensure trust on each other and check the authenticity for proving the integrity of the transaction. With the increase in digital transformation across the globe, it is highly critical to use Public Key Infrastructure for ensuring safe and secure transactions. PKI has vast use cases across several sectors and industries including Medical and Finance.
Explore the complete information about Public Key Infrastructure here
What are important components in Public Key Infrastructure?
There are three key components: Digital Certificates, Certificate Authority, and Registration Authority. PKI can protect the environment using the three critical components. These components play a crucial role in protecting and securing digital communications, electronic transactions.
Digital Certificates:
Most critical component in Public Key Infrastructure (PKI) is Digital certificates. These certificates are used to validate and identify the connections between server and client. This way, the connections formed are very secure and trusted. Certificates can be created individually depending on the scale of operations. If the requirement is for a large firm, PKI digital certificates can be purchased from trusted third party issuers.
Certificate Authority:
Certificate Authority (CA) provides authentication and safeguards trust for the certificates used by the users. Whether it might be individual computer systems or servers, Certificate Authority ensures digital identities of the users is authenticated. Digital certificates issued through certificate authorities are trusted by devices.
Registration Authority:
Registration Authority (RA) is an approved component by Certificate Authority for issuing certificates for authenticated users based requests. RA certificate requests ranges from individual digital certificate to sign email messages to companies planning to setup their own private certificate authority. RA sends all the approved requests to CA for certificate processing.
What are the responsibilities of PKI administrator?
As a PKI admin you will be reporting mostly either to a CIO or a CISO depending on the organization’s hierarchy. Important responsibilities as PKI admin would be to administer the Certificate Authorities (CA) and Hardware Security Modules (HSMs) of the company’s Public Key Infrastructure (PKI) and Key Management. Also, you will be responsible in handling large scale enterprise and commercial/publicly trusted PKI services. Additionally, you are expected to perform and understand the below requirements:
- Administer Windows 2008 R2 and Windows Server 2012
- Active directory services
- Hardware Security Modules
- Certificate lifecycle management – Installation, Renewal, Revoke
- Certificate Enrolment Web Services
These are the core expectations from any firm handling Public Key Infrastructure would have from a PKI admin. Along with these responsibilities, it you would need to manage the Service Level Agreement (SLA) timelines and enhance the efficiency of the process. Currently, there are automated solutions to handle most of the features of PKI. Hence, it is important to have an automation bend of mind to understand, handle and enforce those solutions in the company.
Skillset requirement for PKI Admin
PKI administrator requires quite a good amount of skillsets to handle the day to day activities. This would have been the realization after going through the responsibilities mentioned above. The desired skills for a PKI admin would be as follows:
- PKI hands on experience in handling Certificate Authority Administration, Certificate Enrollment Web Service & Policy Web Service, Active Directory Certificate Services (ADCS) monitoring.
- Data-in-motion and Data-at-rest Encryption.
- Understanding of PKI architecture.
- System Administration of Windows Server 2012/R2 or 2016 and Windows 10, Unix, or Linux, and/or database skillset.
- Expertise in Public Key Infrastructure (PKI) machine identity technologies such as SSH, SSL, TLS.
- Disaster Recovery process and Business Continuity procedures.
- Experience in managing Key Management Systems (KMS).
It is always important and good to have coding skills while handling such critical infrastructure as PKI. Some of the development technologies that a PKI admin should know are Java, PowerShell scripting, Command line tools, HTML, XML, JavaScript.
Knowledge requirement
As PKI administrator you might not be expected to having a complete hands-on experience on the following criteria but you need to have a fair understanding on the concepts of cryptography solutions such as:
- Symmetric/asymmetric cryptography
- Secure hash functions
- Digital signatures
- SSL Certificates
Experience
PKI administrator is a critical position in any company’s cyber security landscape. So, in majority of the cases companies expect the person handling the role of PKI admin to be hands-on experienced on the key responsibilities and skillsets mentioned above in this article. It is expected from you to have a solid experience in PKI, SSL/TLS, and SQL. Other than the direct experience, if you are an IT administrator with cyber security knowledge and skills then there would be higher chances on cracking the opportunity. Just keep in mind that there are no entry level positions for Public Key Infrastructure (PKI) administrator. You would require specialization. Immediately undergo trainings provided by Encryption Consulting or any other reputed certified providers.
Understand the security best practices followed by major firms across industries. Along with the above mentioned responsibilities and skill sets, it would be a major bonus point if you understand what a PKI health check is and how to perform the health checks on a regular basis.
Why should firms worry about PKI Health?
Public Key Infrastructure is not a one-time setup and forget activity. Regular health monitoring is as important as the initial implementation of your PKI as it plays a crucial and deciding role in the firm’s cyber security. PKI Health monitoring and checking activity will ensure that steady state of operations is achieved. Majority of the certificate policies states that an audit has to be performed on a regular basis for safeguarding the compliance of the Certificate Authorities (CAs). It is highly advisable to perform a complete check once a year at least.
Public Key Infrastructure health checks involve multiple steps and factors. Out of all these, some of the important processes that are included in a standard PKI health checks are:
- Patch management and backup
- Certificate checks: Issuing and revoking of certificates
- Auditing of the Certificate Authority
PKI health check benefits
- Performing regular PKI health checks will ensure a strong overall cyber security posture of the organization.
- Operational effectiveness will be monitored on a regular basis by performing PKI health checking activity regularly.
- Compliance with the regulatory standards and frameworks will be ensured as there is periodic check on certificate health.
- Threat vectors of data loss will be reduced considerably with a reduction in risk.
- High availability of critical processes will ensure smooth running of the business.
Encryption Consulting’s PKI training complete package
Encryption Consulting LLC (EC) is offering a complete all-round package on training for Public Key Infrastructure (PKI). This PKI course can be taken by candidate who is at any level – be it a beginner, intermediate level or advanced level. PKI course is recommended for anyone using or managing certificates, designing or deploying a PKI enterprise solution, or evaluating & selecting a commercial PKI Technology Solution.
Planning a Public Key Infrastructure (PKI) can have a significant skill ceiling, as an organization’s authentication, encryption, and digital signing can depend on how the PKI is built. An organization needs a robust and secure PKI infrastructure to ensure security and privacy and meet regulations and compliance. Creating and managing a PKI requires ample knowledge about it, which Encryption Consulting brings along with the experience needed for organizations to have a custom solution for their needs.
In our three days, PKI Training delivered online, In-person focusing on Microsoft Active Directory Certificate Service (ADCS) Training, customers will learn how to deploy or design PKI solutions in the enterprise.
You will learn how to build a PKI on Windows Server 2019, focusing on areas such as integration with HSM, Two-tier PKI, Cloud PKI, and more.
There is a strong emphasis on: PKI Governance, PKI Design best practices, Certificate Lifecycle Management process and PKI operations and hands-on skills lab.