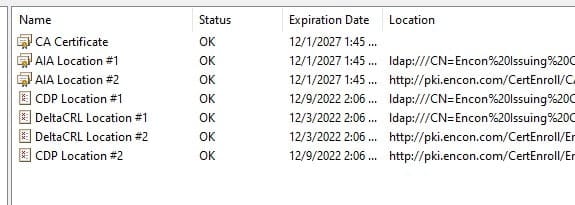
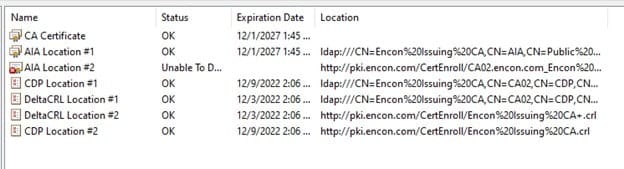
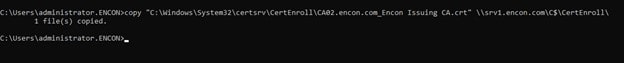
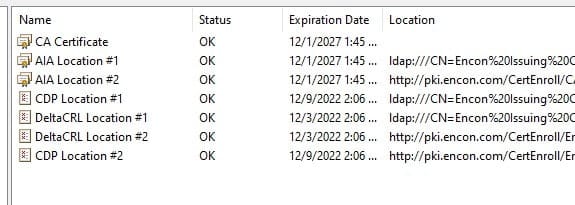
Understanding key management and its importance to your overall security posture is fundamental to establishing the best cryptographic infrastructure for your enterprise. Keys and certificates are used for many different tasks and are vital to your organization’s data security. Your hardware security module (HSM) is like the engine of a car – it’s designed for high-performance cryptographic operations. Key management is like the rest of the car – it’s a combination of the people who operate it, the processes that drive it, and the technology that powers it.
I recently participated in Encryption Consulting’s 2022 Virtual Conference, where I talked about encryption, key management, and how to assess your organization’s key management maturity level. In this article, I’d like to recap some of the latest trends, technologies, and best practices to provide actionable intelligence about key management that you can apply to your organization.
The first step is to assess your organization’s key management maturity level. Then, design a key management-friendly ecosystem and consider factors that may be important for application developers. We’ve developed a key management maturity matrix at Futurex that is extremely useful in this regard, helping organizations self-identify where they rank. The maturity matrix can also help solutions providers determine how to position their technology for better use.
The key management maturity matrix asks organizations to consider these questions:
- How are keys stored?
- Where are keys indexed?
- How is the lifecycle maintained?
- How are audits performed on key material?
- What is your ability to enact crypto-agility concepts?
- How is policy enforced on key material?
Sometimes organizations find that their key management strategy looks like a mess. Still, it’s a good practice to identify exactly where your organization is ranked on the matrix and to work hard to improve that position. That said, the “fully mature, top-right hand of the chart” model isn’t necessarily the best for everyone.
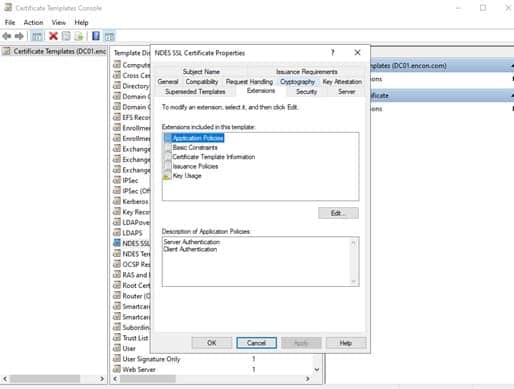
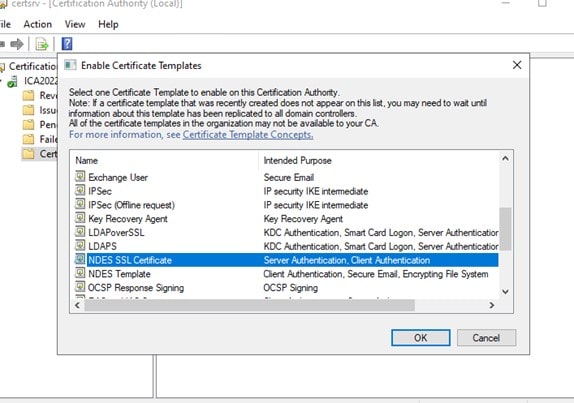
Key Management Maturity Matrix Levels
-
No Key Management Model
This model is typically used after an application is already developed, when someone realizes that cryptographic operations requiring key material are necessary. Often, these keys are stored on developer workstations, or worse, in the software code. The “no key management” model is a terrible one, and introduces considerable risk to an enterprise. This model is also not ideal because the likelihood that anyone will use your products is near zero. What we’ve found is that lack of awareness is the primary reason that some organizations are in this model. Typically, an organization at this level of key management maturity has an IT team that lacks a fundamental awareness that there is a problem at all. Education is very important at this level.
-
Application-specific Key Management Model
Applications either develop tools or implement application-specific third-party tools. At this level of key management maturity, HSMs may be used to secure key material, but keys may be software-based. As this is enforced by the application, users are dependent on the application capabilities.
-
Semi-Centrally Managed Key Management Model
In this semi-centrally managed key management model, an organization has typically deployed a system that is capable of centrally managing keys. However, one or two problems may occur. On one hand, the tool that they’ve deployed might not be extensive from a capability standpoint and the enterprise is limited on what applications can interface with it. On the other hand, an organization might have deployed a mature system with a large offering from a compatibility standpoint, but they are still in the process of migrating applications to it.
It’s at either stage where we see a “valley of despair” effect. Sometimes there’s a real disparity between the architects who design the system and the rest of the organization. You can have all the technology in the world, but if it’s too complex to implement and requires your CFO to write a check with six zeroes on the end to actually see its full benefit, there’s a good chance it will go nowhere.
At Futurex, it’s our job as security architects and technology executives to make sure we take this into account. It’s not enough to say, “Here, I’ve built a Ferrari engine, now you figure out how to build the car around it.”
-
Hardware-Backed, Centrally Managed Key Management Model
At this level of hardware-backed, centrally-managed key management model, an organization has implemented a robust, service-oriented architecture for its cryptographic infrastructure.
Where is your organization in the Key Management Maturity Matrix?
There are several factors that drive an enterprise’s key management maturity level:
- The organization culture from the top down when it comes to application security and cryptography.
- Regulatory and audit requirements.
- Applications needs
Application needs and requirements typically are the primary driver as application developers require cryptographic keys. Developers and project owners who are aware of common cryptographic attacks and key management principals will commonly go to the security team to discuss organizational policies for managing keys. As these requests increase, a need for a more mature key management model is realized.
When organizations fully realize that centrally managed key management infrastructure is critical, there is often the challenge to deploy it enterprise-wide. After this realization, a tool is deployed and the journey of moving key management activities to the new infrastructure begins.
For example, we’ve helped ATM service providers disentangle key management from their ATM transaction processing infrastructure to allow them to centralize the security and management of their key lifecycle. In addition, there are many other examples which are not industry-specific, such as developing automation tools that ease deployment of new applications. We’ve found that, with the right knowledge and tools, any organization can get over the hump to a hardware-backed centrally managed infrastructure.
There are several best practices that make key management easier. One of the main requirements of your key management infrastructure is that it should absolutely be powered by robust hardware. You can’t fully “harden” your solution without dedicated hardware certified under the strictest international compliance requirements, such as PCI PTS HSM v3 and FIPS 140-3 Level 3. Your solution also needs to support all of the key management use cases for your organization. You don’t want to let your key management policies start fragmenting. As complexity grows, costs rise and security weakens.
With the wrong tool, your access control policies can easily feel like a tightrope with the wrong tool so you should make them granular enough without making them too overburdensome to manage properly. Most importantly, the lifecycle of your keys, which varies not only from organization to organization but use case to use case, needs to be properly enforced. You need “crypto-agility” to apply your existing infrastructure to new projects with minimal investment.
What application integrations are important to your organization?
Application integrations with Oracle TDE, Microsoft SQL TDE, VMWare vSphere, Apache Tomcat, Google Workspace, and other custom data protection applications should all be considered to determine what makes sense for your organization. The next step is developing a timeline for migrating to a centralized key management infrastructure and determining order.
You’ll want to configure the key management server, define which endpoints have access to use the keying material, define how that access is granted (whether by an external identity provider or newly generated credentials), and configure the application itself.
As you can see, the process of implementing best practices for your organization’s key management can be made much easier with the expert guidance and tools from Futurex. We’re looking forward to the opportunity to help you and your organization along your key management journey.
To learn more about Futurex’s key management solutions, visit Key Management