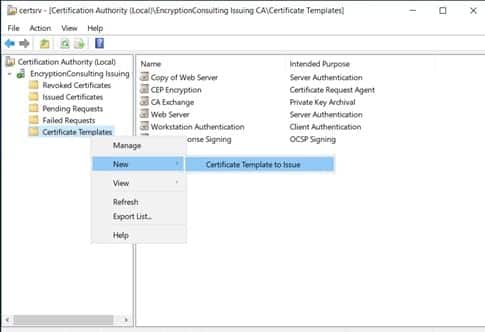
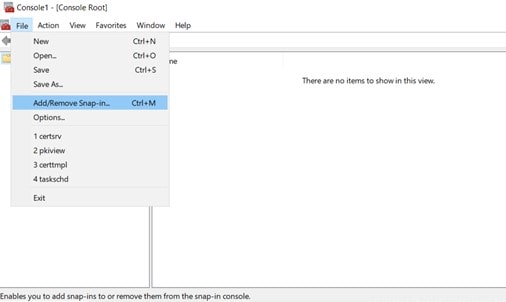
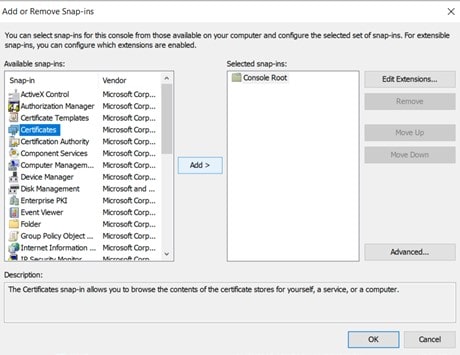
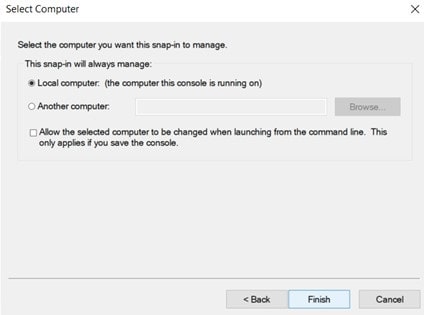
Within the network, constant communication is always happening while using computer systems and software. There must be various components for this communication mechanism to function. A telephone, for example, requires a sender, a receiver, and a signal to connect the two ports. They contain unique numerical addresses that allow the system to determine where the information is transmitted.
These ports are configured to guide traffic to the appropriate destinations; in other words, they are the assistants that instruct systems engaged in determining which service is being sought. Services vary from unencrypted HTTP web traffic on port 80 to FTP on port 21, which transports data and files between servers and clients.
There are 65,535 ports, although not all of them are used daily. On the other hand, the TLS/SSL port is one of the most regularly used ports and is almost certainly utilized daily. So, what port does TLS/SSL use? The TLS/SSL port is 443, HTTPS, and employs TLS/SSL certificates to safeguard port communications. HTTP is the unsecure protocol port (port 80).
What are the most often used TCP ports?
Managing TLS/SSL certificates necessitates a thorough understanding of security and network connectivity. Knowing some of the most frequent TCP (or transmission control protocol) ports may be important.
For your convenience, we’ve created a list of these popular TCP ports and their functions.
Unsecured port numbers with their function:
- 80, HTTP
- 21, FTP
- 119, NNTP
- 389, LDAP
- 143, IMAP
- 110, POP3
Secured port numbers with their function:
- 443, HTTPS
- 990, FTPS
- 563, NNTPS
- 636, LDAPS
- 993, IMAPS
- 995, POP3S
What Is the Purpose of Port 443?
As previously stated, TLS/SSL certificates secure port 443 communications. The primary role of TLS/SSL certificates is to protect information so that online traffic or cybercriminals cannot access it. This is why many businesses choose HTTPS over HTTP to safeguard their data from being exposed or compromised while it is being transferred and received.
SSL vs. TLS and HTTP vs. HTTPS: How do they function together?
SSL vs. TLS
SSL certificates are a defunct word for what is now known as TLS certificates. They fundamentally provide identical security duties, yet many individuals continue to use the word SSL while others use TLS. It’s vital to keep in mind that they aren’t different, which is why certificates are commonly referred to as TLS/SSL, so that people understand that they are not different.
HTTP vs. HTTPS
HTTP and HTTPS are not two distinct protocols. Rather, HTTPS is a specialized form of HTTP that employs TLS/SSL certificates. HTTPS is thus simply a safer version of HTTP that is safer to use while transferring data.
How do they function together?
The default network will begin with HTTP. To protect your network, you must install a TLS/SSL certificate on the web server that you are using. After that, the certificate will confirm your organization’s identity in order to launch the HTTPS protocol. This ensures that data is safely sent from a web server to a web browser.
Why are SSL ports necessary?
You may be asking why your network server needs an SSL port over other ports and internet connection techniques. TLS/SSL certificates will be your most dependable ticket to secure data transport. While safety is paramount, there are a few additional factors to consider:
-
PCI compliance requires the use of HTTPS:
In order to accept any form of online payment, you must be PCI compliant. This will also protect both your data and the information of your customers.
-
HTTPS is faster than HTTP
If you have a TLS/SSL certificate-protected page that is HTTPS, your information will most likely load significantly faster than it would on an HTTP website.
-
Cybercrime
With more businesses, consumers, and internet hackers utilizing the internet on a daily basis, it’s reasonable to assume that security is more important than ever. Using an SSL certificate port to secure your organization is one of the finest preventative actions you can do when it comes to cyber security.
Managing TLS/SSL Certificates
Keeping your apps safe frequently boils down to good TLS certificate management. The use of TLS/SSL certificates is a critical initial step. However, many businesses overlook the need to safeguard their systems against compromise and misuse.