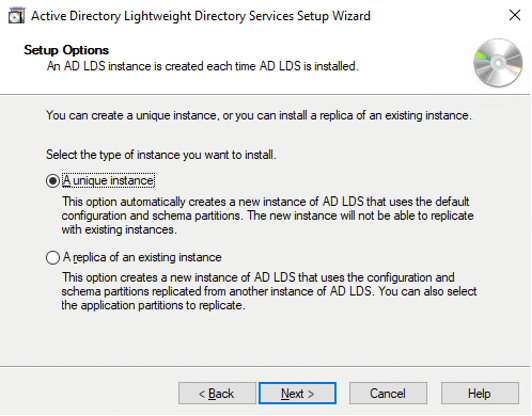
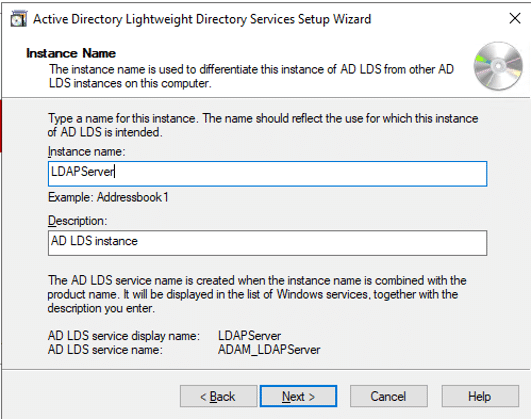
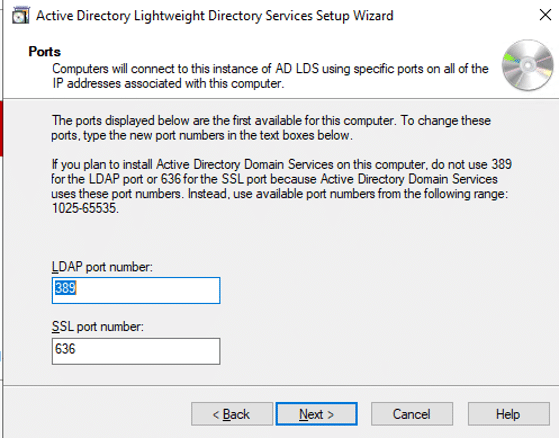
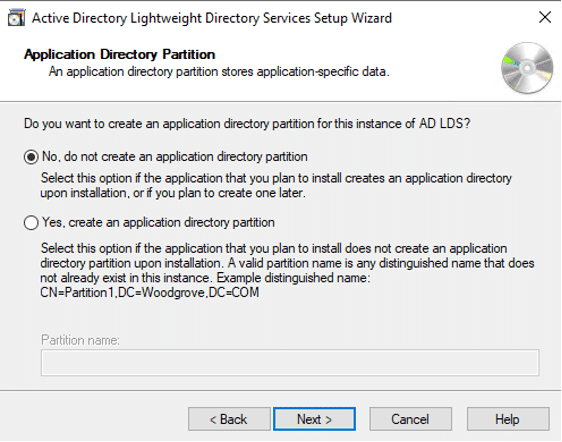
Trust is crucial in the software-driven society we live in. But how can we tell which software to rely on and which to avoid? We can thank code signing for that.
Developers use code signing to demonstrate a piece of software’s legitimacy and ensure that it originates from a reliable source and hasn’t been tampered with. Cryptography, more especially a certificate known as a code signing certificate, is necessary for code signing.
Customers should constantly be on the lookout for third parties posing as software providers while downloading software from the Internet. Software may be ensured that it is coming from the right source with the use of a tool like code signing. To ensure that consumers are receiving software that accomplishes what its creator claims it will, code signing is a process where a software developer or distributor digitally signs the file being sent out. The signature indicates that the code has not been altered from its original state.
Benefits of Code Signing
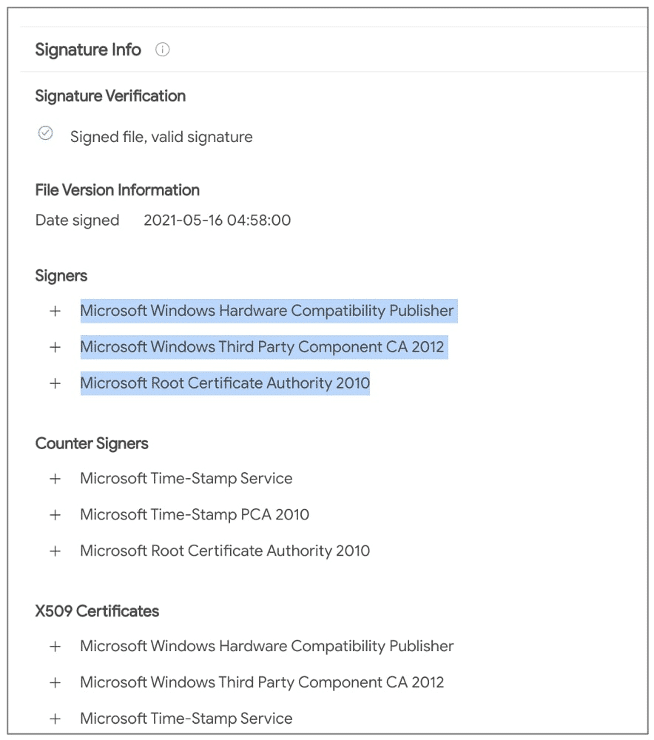
Code signing is a technique for adding a digital signature to a program, file, software update, or executable so that, upon installation and execution, its validity and integrity can be checked. It ensures to the receiver who the author is and that it hasn’t been opened and tampered with, much like a wax seal. To demonstrate, for instance, that your Windows 10 update genuinely came from Microsoft and not a hacker attempting to breach your machine, Microsoft developers, programmers, and software engineers utilize code signing.
You can be confident that you are downloading a file from a legitimate author or publisher and not from an attacker trying to steal your personal information and data thanks to code signing. In essence, it informs you that a bad guy hasn’t changed the code so you know it’s safe to install and run on your machine.
If you’ve ever seen the small window that appears when you attempt to launch a software you’ve downloaded, the one that asks, “Are you sure you want to run this? ” and identifies the publisher, then you know what I’m talking about. then you have experienced code signing. That dialogue box informs you that the patch for your Mac OS X is authentic and still in the same state as when it was signed by Apple Inc.
What Does Code Signing Do?
As a user, code signing serves a few distinct purposes that might assist you in determining if you should trust software downloads and other online interactions. Code signing is mostly used to verify the authorship of files, downloads, and software. For instance, you are more likely to install a download file supplied to you from Microsoft than one from any other source since it will seem to be much more reliable.
There will inevitably be updates for the software you install on your computer in the future. You may be sure that subsequent updates have come from the same source and are secure to run on your computer when they are code signed with the same key that was used to “seal” your initial downloads.
How Does Code Signing Work?
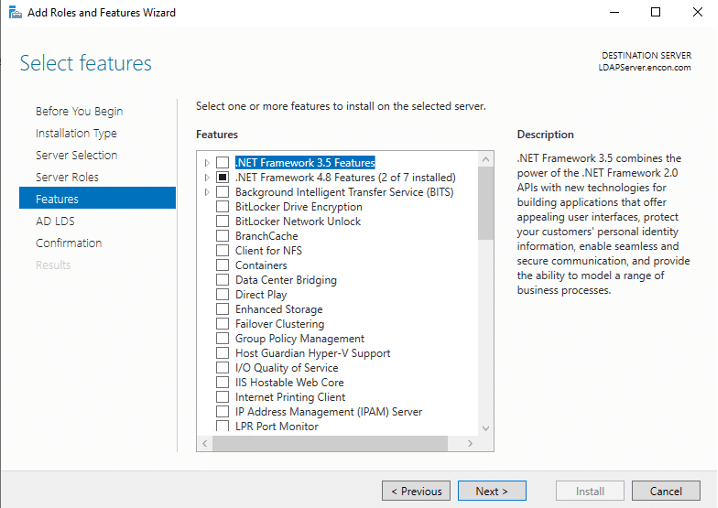
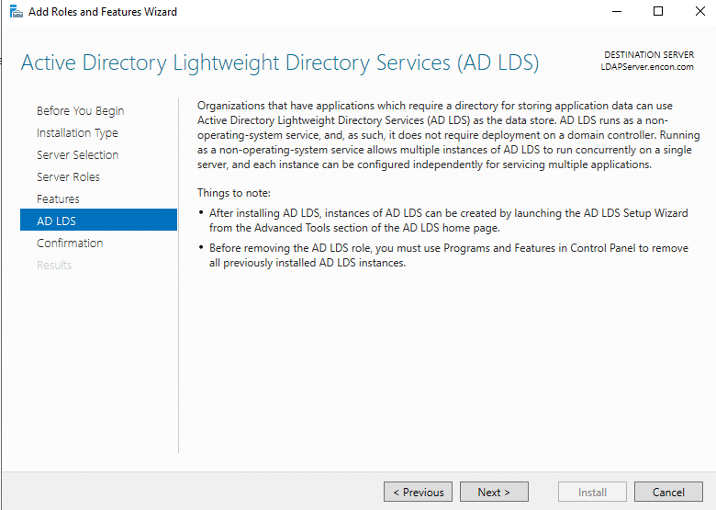
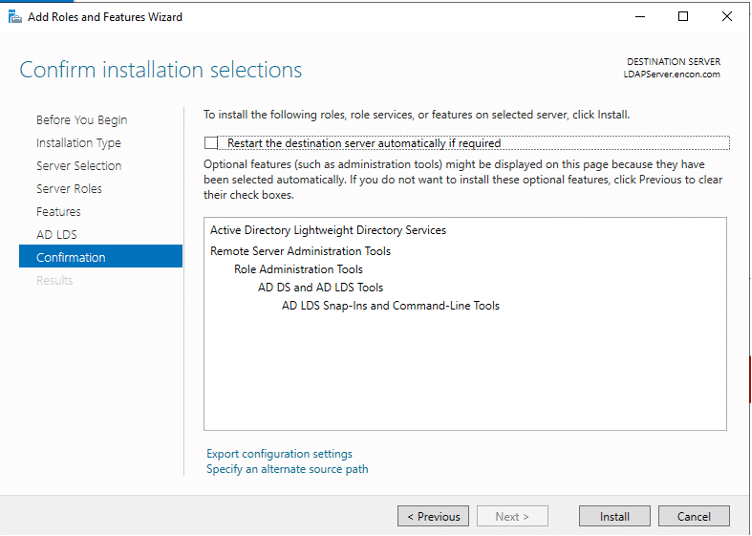
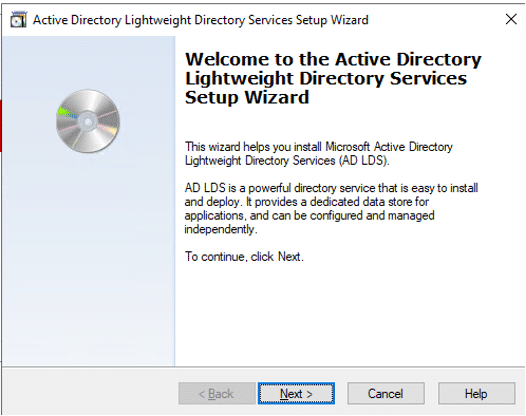
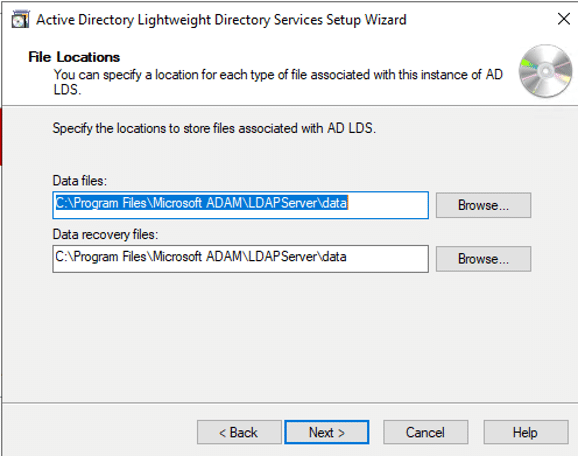
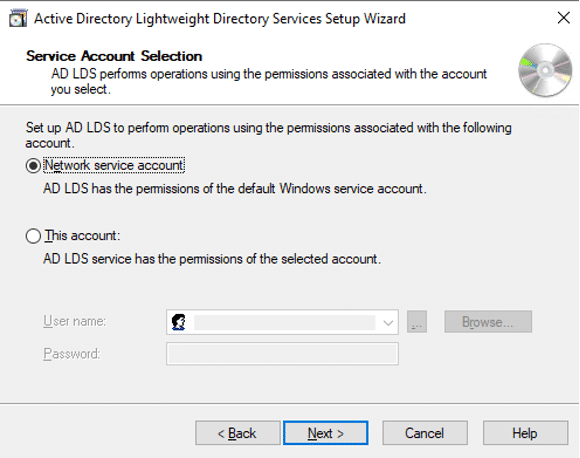
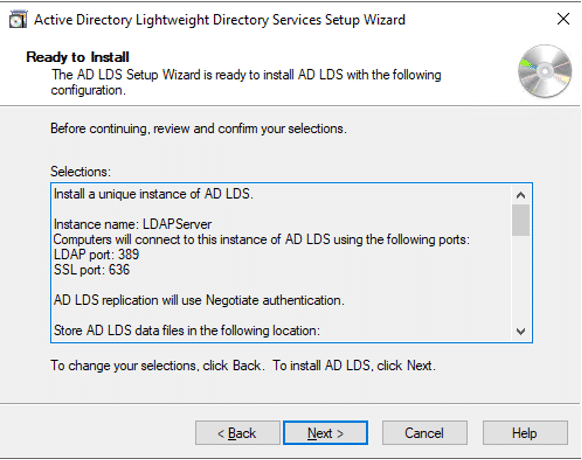
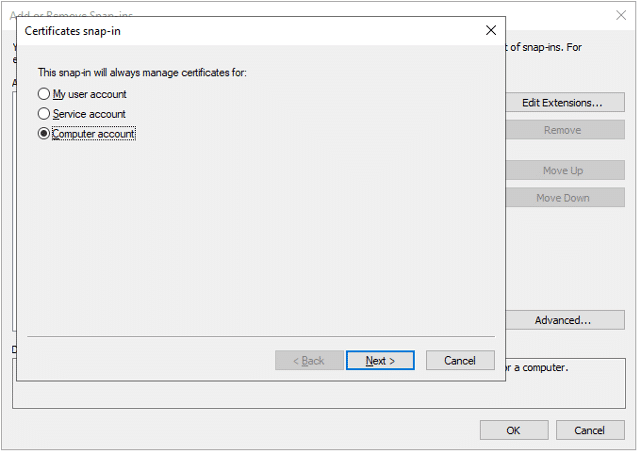
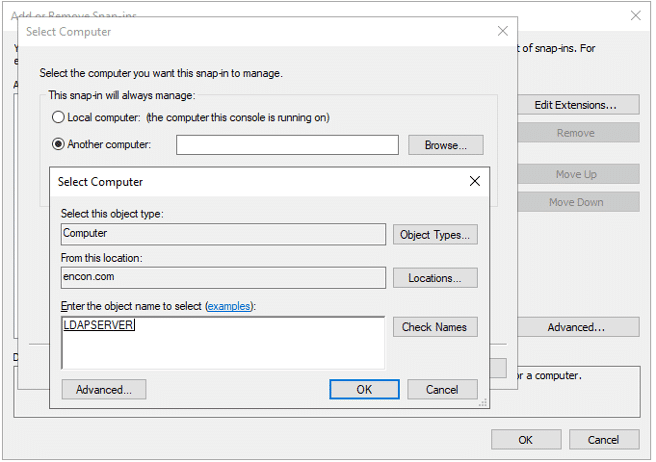
From the perspective of a developer, code signing has three main parts: unsigned software files; code-signing certificates; and code-signing apps. Applications for code signing are typically included with operating systems like Microsoft Windows, Mac OS X, etc. Certificate Authorities are frequently the source of the code signing certificates (CAs).
Public Key Encryption
When you encode a message to shield it from unauthorized viewers, you are using encryption. Decoding the message depends on knowing the key that puts the values back to their original state, enabling the message to be read. Typically, this is done by running it through a mathematical function (referred to as a “key”) to alter values. The key that encrypts the message and the key that decrypts it is distinct in public key encryption (also known as asymmetric encryption) (hence asymmetrical). It is known as a “public key” system because only one key—the “public key”—is used to secure the communication, while the other—the “private key”—is kept secret.
Private keys must be kept secure, confidential, and out of the hands of anybody who would try to intercept or tamper with messages in order for this type of encryption to work. The kind of transmission determines whether the public key is used to encode or decode the message. Encrypt using the private key and decode with the public key if you want everyone to be able to read the message but don’t want anyone to tamper with it. You encrypt using the public key but decode with the private key if you want everyone to be able to send messages but don’t want them intercepted by the incorrect person.
Hash Function
A form of encryption called hash functions is intended to be irreversible. Hash functions are designed to be one-way, utilizing a mathematical function that modifies the data in a way that can’t be undone, as opposed to encoding with a key and using a key to decode. The most typical comparison is like mixing paint. As an illustration, mixing blue (the original values) and yellow (the hash function) will always result in green, but there is no way to separate the two colors and get back the blue.
When you require a set value and don’t need to read the data again, hash functions are utilized. The most prevalent example is login passwords, which are frequently hashed by websites for storage. If there is ever a breach, all the hacker has obtained is a collection of random numbers. The website hashes your password once again and compares it to the previously saved hash value when you log in. They let you in if the information you provided matches what is in their records. They only need to know the value; they don’t need to read the password itself.
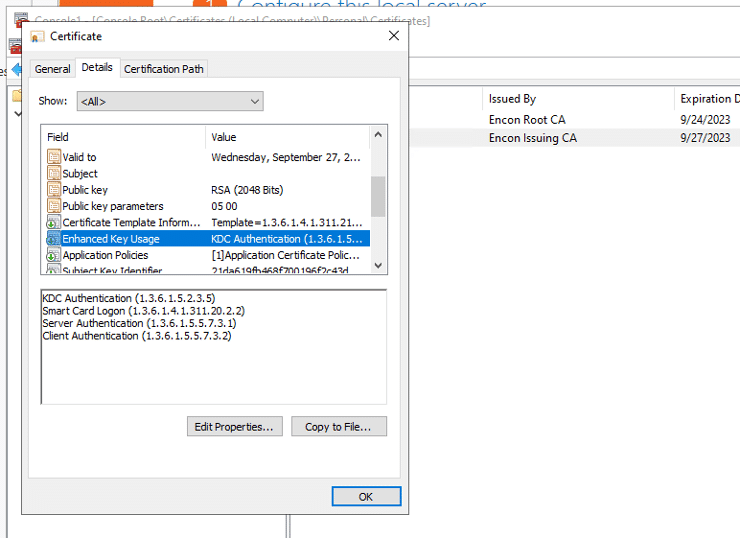
Code Signing Certificates
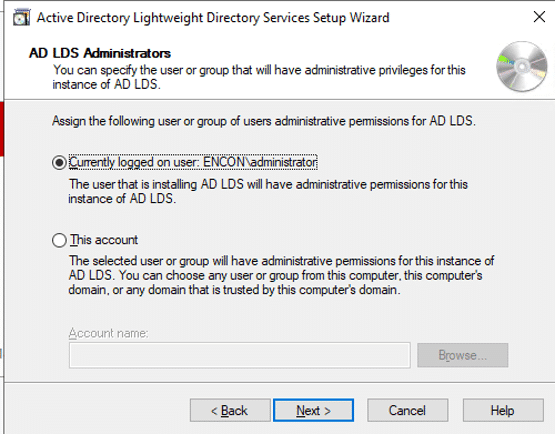
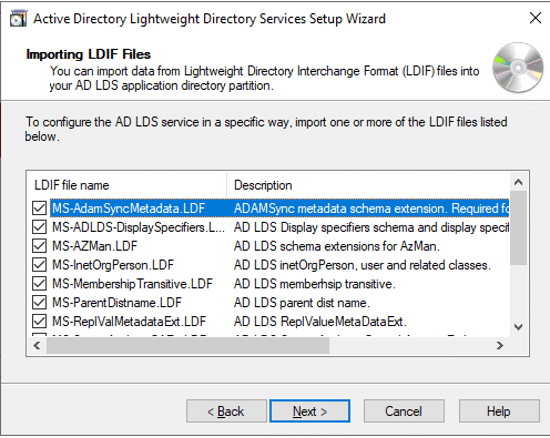
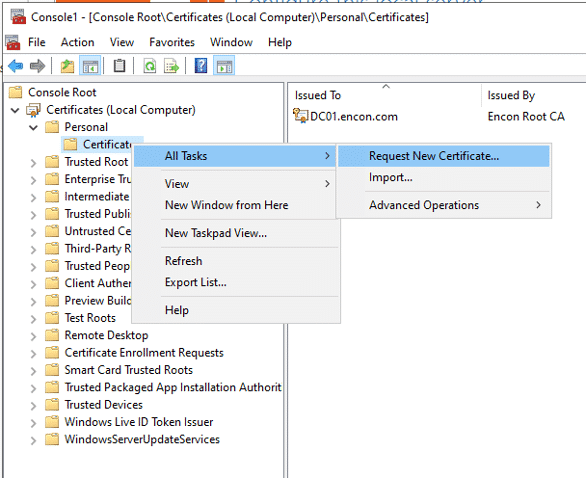
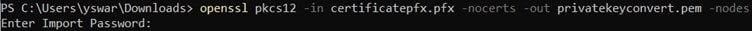
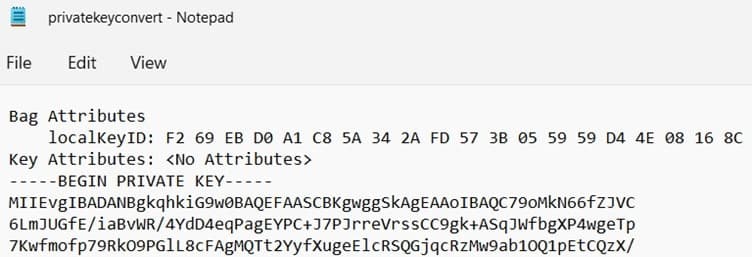
Before the developers can sign their work, they need to generate a public/private key pair. This is often done locally through software tools such as ‘OpenSSL’. Developers then give the public key and the organization’s identity information to a trustworthy CA. The CA verifies the authenticity of identity information and then issues the certificate to the developer. This is the code signing certificate which was signed by CA’s private key and contains the developer organization’s identity and the developer’s public key.
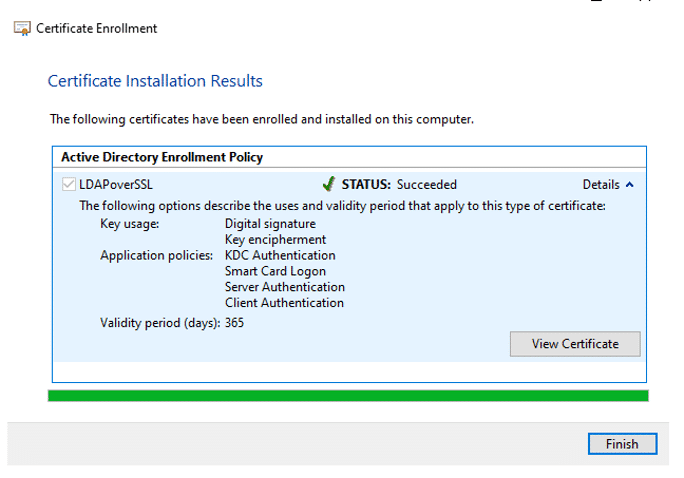
Developers take all the code they produced and hash it when they’re ready to “sign” it to prove authorship. The output value is then encoded using the previously stated private key, which is often created by the author, as well as the code signing certificate, which contains the public key and the author’s identity (proving the authorship). The result of this procedure is then included in the program that will be distributed.
This is an instance of code signing. The majority of browsers and operating systems come with the public key of the CA pre-installed. When a user downloads the program, they first authenticate the legitimacy of the code signing certificate incorporated in the signed software to ensure it’s from a reliable CA using the CA’s public key. The encrypted hash is then decrypted using the developer’s public key, which is subsequently taken out of the certificate.
The program is then hashed once more, and the result is contrasted with the decrypted value. The program has not been tampered with or damaged during transmission if the hash values generated by the user and the developer coincide. The user is then informed that the program is in the same condition as when the developer last left it and that it is safe to install and execute if the developer can be believed.
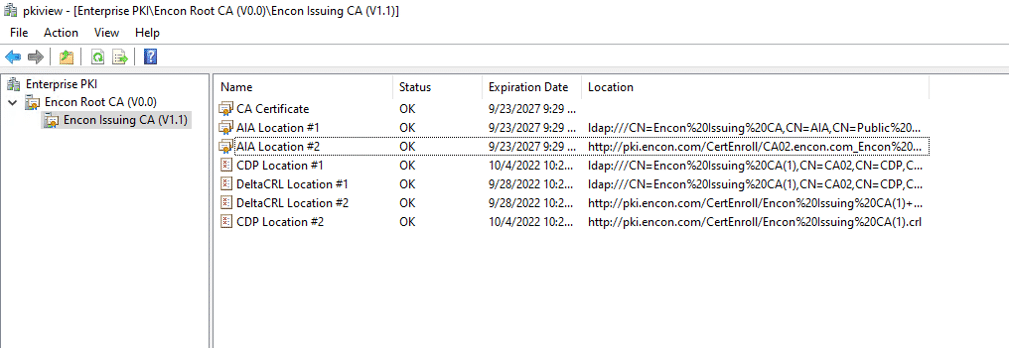
Root Certificates
Code signing can provide you, the end user, confidence in the reliability and validity of the downloaded program. However, you should also be mindful that malicious actors may produce a code signing certificate and a public-private key pair to give the impression that they were authorized by a legitimate CA. How do you determine whether certificates are reliable if anybody can create a code signing certificate?
Root certificates have a role in this. Code signing certificates can be compared to a family tree. You may trace certificates back to discover which signing certificate—your root certificate—is at the root of the tree in order to confirm where they originated. Because you can follow the “chain of trust” back to the initial signing authority with the root certificate, you can tell whether the other code signing certificates are reliable.
Enterprise Code-Signing Solution
Get One solution for all your software code-signing cryptographic needs with our code-signing solution.
A business like Apple or Microsoft might be considered the root authority. The system will warn you not to trust the certificate that was used to sign the program you are attempting to download if your software’s signing certificate is unable to locate a reliable root certificate. Even a trusted authority may occasionally fail to be recognized if it is not installed on a browser or in the trust store of an operating system. For the browser or operating system to accept the root certificate as reliable and valid in these situations, you will need to manually put it on your trust store.
What Are the Types of Digital Certificates?
Different systems require different types of authentication. What works on a desktop is likely unsuitable for mobile systems and vice versa. Here are a few examples of the different certificates for both desktop and mobile software.
Desktop Certificates:
- Microsoft
- Java
- Microsoft Office and VBA
- Adobe AI
Mobile Certificates:
- Windows Phone
- Windows Phone Private Enterprise
- Java Verified
- Android
If you’re looking to sign and secure your software, you should first know what kind of software or system you are starting with and work from there.
What is the Use of a Digital Certificate?
A digital certificate is meant to provide the software or code you’re distributing to your users with an identity. Users can verify the program publisher using a digital certificate. Because these digital certificates are issued by certificate authorities, users have more faith in the publishers. The ability to track their product and the number of downloads gives digital certificates to software providers a lot of additional value.
How Long is a Digital Certificate Valid?
How long a certificate is valid is another typical query from those trying to obtain their own digital code signing certificate. Digital certificates normally only have a year or two of validity, however, the actual duration might vary depending on the issuer.
This validity is brief for the following two reasons:
Private keys and security certificates may and do become hacked. Any prior certifications, even those that have been stolen, become invalid upon renewal and change every year or two.
Technology is evolving at an even quicker rate than the rest of the globe. Five years ago, what was secure is no longer nearly as secure. Code signing certificates can be updated and changed to keep the certificate security current.
Where is Code Signing Used?
Code signing is used any place a developer wants a user to be sure of the source of a piece of software. This includes:
1. Windows applications and software patches
2. Apple software
3. Microsoft Office VBA objects and macros
4. .jar files
5. .air or .airi files
6. Essentially any executable
Be aware that, because of the distributed nature of Linux development, code signing is often not used for Linux-based software, so that software may come unsigned. If that happens, your computer will (if it gives any notice) will tell you it’s from an “unknown developer,” or something along those lines. Here are a few other applications and software that utilize code signing to increase their security.
- iOS: Code signing in iOS for the App Store is done using Xcode. The purpose of signing your app is simply to let iOS know who signed the app originally and to make sure it hasn’t been altered since it was originally signed by the developer. If you need to revoke your iOS certificate, you will need to use your developer account or Xcode to complete the process.
- Xcode: Xcode is used by iOS to code sign apps and ensure their security. Before any device can be uploaded and approved for the iTunes store it must have a valid Apple Developer ID with a valid certificate or profile. To successfully integrate your app, you will need to use a development certificate. In order to run the app on any device, you must use a distribution certificate to send out the app and test it.
- C#: Visual C# uses strong name signing to get a unique sign code that is not available to anyone else in the world and cannot be spoofed. When using Visual C#, you can simply sign your deployment using the sn.exe tool. This functions as your signature by using sig check tool printing “Strong Name: Signed.”
- Windows Certificate: Nearly any executable can be signed with a digital signature to verify the security and integrity of the file. For the file to be considered secure in Windows, it must be signed by a recognized certificate authority. Anyone who distributes malware under a valid certificate is held legally accountable for the software they distribute.
- Visual Studio: Visual Studio is particularly helpful when it comes to strong name signing for assemblies—a notoriously difficult task. Strong name signing through Visual Studio allows other computers to trust the software developer.