Introduction
Threats loom ever present in our digital world, which is why methods of securing data are constantly advancing. Tactics like encryption are used every day on sensitive data-at-rest or in-motion. Encryption is the process of putting data in the form of plaintext into an encryption algorithm, and producing a ciphertext. Ciphertext is a form of data where all the patterns of letters that create words in the plaintext are scrambled into a new text that cannot be read without decrypting the data. Encryption uses a key to ensure the ciphertext cannot be deciphered by anyone but the authorized recipient.
Signing of data works to authenticate the sender of the data and tends to implement a form of encryption in its process. The process of signing emails, sensitive data, and other information has become necessary, as it verifies the identity of the sender and ensures the data has not been altered in transit. If a Man in the Middle attack occurred and the data was altered or compromised by the attacker, the recipient of the information would know that this has occurred. The attacker could alter the data, but as they do not have the key used by the sender to sign the data, the recipient of the data will know not to trust the sent data when analyzing the key and data.
How does digital signing work?
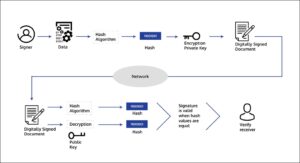
The process of digital signing works similarly to encryption. Encryption comes in two types, asymmetric and symmetric encryption. The process of asymmetric encryption works by creating a key pair with a public and private key. The private key is kept secret from everyone but the creator of the key, while the public key is available to everyone. The data is encrypted with the private key, and decrypted when needed with the public key. Symmetric encryption only uses one key for both encryption and decryption. As asymmetric encryption is more secure than symmetric encryption, it tends to be used more often. When sending data to a recipient, the correct method of encryption is to encrypt the data with the recipient’s public key, as this means only the owner of the key pair can decrypt that data.
Digital signing works oppositely. The data is signed by hashing the message with a hashing algorithm and the sender’s private key. This produces a hash digest, which can only be recreated through use of one of the keys in the key pair created by the sender. The recipient then receives the message, the hash digest, and the public key, if they did not already have it. The recipient then uses the sender’s public key to hash the message they have received. If the resulting hash digest matches the hash digest that has been sent along with the message, then the identity of the sender has been confirmed. This also confirms that the data has not been changed in transit. However, signing alone does not ensure the data has not been intercepted and read.
Encryption and Signing
To protect data from compromise and authenticate the sender at the same time, encryption and digital signing are used together. They are also both used in tandem to fulfill compliance standards for companies. Standards, like the Federal Information Processing Standards (FIPS) or the General Data Protection Regulation (GDPR), require companies to protect data as securely as possible along with authenticating data received from others. Encryption and digital signing ensures these standards are reached, and that users can be secure in the knowledge that data that is sent to and from them will not be compromised.
Confidential or sensitive data should always be encrypted and signed for its own safety. The use of encryption and signing together ensures that the main goals of cryptography, Confidentiality, Integrity, Authenticity, and Non-Repudiation are all met. Confidentiality and integrity are reached when data is encrypted asymmetrically, as only the intended recipient can decrypt the message. Non-repudiation and authenticity occur due to digital signing. Non-repudiation means that using the technique of digital signing, the sender of any information cannot, in the future, say they did not send the data, as the use of their private key confirms that they sent the data.
Common Encryption and Signing Algorithms
Symmetric Encryption Algorithms:
- Advanced Encryption Standard (AES)
- Blowfish
- Twofish
- Rivest Cipher (RC4)
- Data Encryption Standard (DES)
Asymmetric Encryption Algorithms:
- Elliptic Curve Digital Signature Algorithm (ECDSA)
- Rivest-Shamir-Adleman (RSA)
- Diffie-Hellman
- Pretty Good Privacy (PGP)
Signing Algorithms:
- RSA
- ElGamal Encryption System
- Digital Signing Algorithm (DSA)
- ECDSA
Why should you use digital signatures
Digital signatures offer several advantages in the realm of information security and authentication. Here are some key reasons why you should use digital signatures:
-
Authentication
-
Identity Verification
Digital signatures provide a way to verify the identity of the sender or creator of a digital document or message. This is crucial for ensuring that the information has not been tampered with and comes from a trusted source.
-
Non-repudiation
Digital signatures make it difficult for the signer to deny their involvement in creating or sending a document. This is important in legal and business transactions where proof of origin or consent is needed.
-
-
Integrity
Digital signatures ensure the integrity of the signed data. If any changes are made to the document after it has been signed, the signature becomes invalid. This helps to detect and prevent unauthorized alterations to the content.
-
Data Integrity
Digital signatures not only protect the integrity of the document but also ensure the integrity of the entire data transmission. Any tampering during transmission can be detected through signature verification.
-
Non-repudiation
Non-repudiation is a key concept in digital signatures. Once a document is signed, the signer cannot deny their involvement or claim that they didn’t sign it. This is crucial in legal and contractual contexts.
-
Efficiency and Convenience
Digital signatures streamline processes by eliminating the need for physical signatures and paperwork. This leads to faster and more efficient transactions, especially in the digital business environment.
-
Security
Digital signatures use cryptographic algorithms to secure the signing process. As a result, they are highly resistant to forgery and tampering. The use of private and public key pairs adds an extra layer of security
-
Compliance
In many industries and regions, the use of digital signatures is mandated by laws and regulations for specific types of transactions. Adhering to these standards ensures compliance with legal requirements.
Conclusion
Encryption and digital signatures are robust security measures and complicated to manage. CodeSign Secure from Encryption Consulting simplifies signing individual files, whole applications, or codes in batches. It also manages digital certificates, timestamps the code for immutability, and guarantees broad platform compatibility for signed code.
CodeSign Secure goes beyond basic code signing by providing enhanced security features and robust audit trails. It is CA/Browser Forum standard-compliant following to assure the credibility of the code signing certificates. It also supports the automation of the code signing process by allowing integration with the software development and deployment pipelines. CodeSign Secure offers diverse access controls and provides a safer environment with enhanced transparency to perform code signing efficiently.