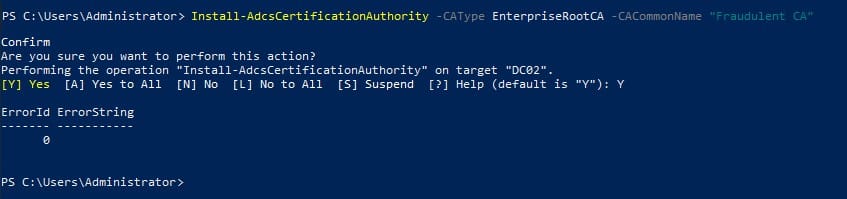
SSL certificates are a vital entity in secure internet communication, as they help browsers and users ensure that the websites, they are interacting with are legit. You can think of these digital certificates as digital IDs that verify a website’s identity and legitimacy.
Whenever we connect to a website through an HTTPS connection, our browser checks the digital ID (certificate) with a trusted source thus performing these tasks at the backend. This whole process, specially verifying the certificate’s signature helps the browser verify whether we are on a real server or a fake one.
However, there are some situations in which a signature can’t be trusted. In those cases, a mechanism called Revocation comes into play. Revocation allows the browsers to know when a certificate is no longer safe to use. This could be due to server compromise, manual human error, or any other security issue.
Certificate revocation is a process by which a Certification authority invalidates an SSL certificate. Once a certificate is revoked, that certificate can’t be used to create a secure connection. Users are also notified about the revocation list to handle any potential security risk.
But why would a CA revoke a certificate? The most common reason for this is that the user/ entity holding that digital certificate requests its revocation. Another reason is that the CA realizes it has issued the certificate in error. The common thing in both scenarios is that revoking the certificate is crucial to prevent security vulnerabilities that could be easily exploited.
Now, the main thing to note here is just revoking the certificate isn’t enough; this must be communicated to the end user as well. This is where OCSP Stapling comes into play.
What is OCSP Stapling?
Online Certificate Status Protocol (OCSP) stapling is an internet standard that is used to verify the revocation status of X.509 certificates. This process involved periodically sending status requests to the certification authority (CA) and then passing the response to the browser for verification. Whenever a client wants to connect to the server, it presents a response validating the revocation status.
This approach ensures that the browser can quickly verify whether the certificate is valid or revoked without contacting the CA directly. If the browser receives a “revoked” status, it alerts the user to prevent the communication of any confidential information with the server.
How does OCSP Stapling work?
Following are the steps involved in the working of OCSP:
-
Certificate Issuance
Before the connection, CA issues a certificate that includes an OCSP supporting indicator. This lets our browser know it should use OCSP for the revocation checking. Also, this is a mandatory standard, requiring all the CAs to provide an OCSP service and issue certificates that support OCSP.
-
OCSP Responder Updates
The CA publishes the certificate validity status to an OCSP Responder. This server is operated by the CA and handles all the OCSP requests. The CA updates the OCSP information for each certificate it has issued, including the revoked ones, at least every four days.
-
SSL Handshake
The SSL Handshake between the client and server happens, involving several steps to establish the connection.
-
Fetching OCSP Response
The server fetches a response from the OCSP Responder. This response contains the certificate validity information and can report any of the following three statuses: good, revoked, or unknown. Now, the browser caches this response up to ten days and then after again calls the responder for a response.
-
Stapling the OCSP Response
The server “staples,” i.e., attaches the OCSP response to the digital certificate and sends both to the browser. This is the key difference from vanilla OCSP, where the client is responsible for obtaining the OCSP response directly from the OCSP Responder, which can cause delays and security issues.
-
Completing the Handshake
Then the SSL Handshake completes, and the OCSP response indicates “good” or “revoked” status based on the certificate.
-
Secure connection Established
If everything checks out, then the connection is established, and secure communication begins.
Certificate Responses
Following are the possible responses with OCSP stapling:
- Revoked: If a digital certificate is revoked, then the browser will show a warning. This response is a hard stop because the browser immediately terminates the connection.
- Good: A good response is when the OCSP responder recognizes the certificate serial number and finds that it is valid.
- Unknown: This message is displayed if the OCSP responder doesn’t recognize the certificate. This is the case when the responder needs access to the CA that issued the certificate in question. This is a soft stop because it may (or may not) allow the connection to go through.
Advantages and Disadvantages of OCSP Stapling
Advantages of OCSP Stapling
-
Improved Performance
Unlike the conventional Certificate Revocation Lists (CRLs) method, OCSP stapling doesn’t slow down browsing performance. The server downloads and caches a copy of the OCSP response from the OCSP responder, reducing latency for the user.
-
Speed and Efficiency
OCSP stapling offers improved speed and performance in verifying the revocation status of a digital certificate. It takes minimal time to verify the status and establish a secure connection.
-
Enhanced Privacy
OCSP stapling provides users with better privacy than traditional OCSP responder queries. As the CA or the OCSP responder can’t see the websites visited by the client, user privacy is better protected.
-
Resource Optimization
OCSP stapling consumes fewer network resources compared to CRL or traditional OCSP, making it a more efficient solution.
Disadvantages of OCSP Stapling
-
Dependence on OCSP Responder
If the OCSP responder experiences downtime for any reason, web servers won’t be able to generate the latest OCSP response. This creates a single point of failure and could lead to browsers being unable to update about the Revocation.
-
Limitations in Certificate Verification
OCSP stapling typically doesn’t provide verification for intermediate certificates in a certificate chain. However, newer versions like multi-stapling and TLS 1.3 support are resolving this limitation.
-
Periodic Updates
There is a time gap between OCSP stapling responses, leaving the servers unaware of new revocations during this period. If a certificate is revoked during this time, outdated responses may be provided.
-
Privacy Concerns
The verification process may leak information about the content a user is accessing, which may be used to track user behaviours and cause privacy issues.
How to check for OCSP Stapling
Ensure you are using Windows Server 2008 or above.
- Windows server beyond 2008 support OCSP Stapling by default while versions below 2008 don’t support OCSP Stapling.
- If you are using a windows version below 2008. Please upgrade to 2008 or above to enable OCSP Stapling.
Step 1: Go to SSL Labs by Qaulys.
Step 2: Check the box “Do not show the results on the boards.”
Step 3: Enter the domain name you want to check and click on Submit.
Step 4: After the scan gets completed. Review the “Revocation Information”. This section will include CRL and OCSP details.
Step 5: In the OCSP Stapling row:
- If it says, “Yes” then OCSP Stapling is enabled.
- If it says,” No” then OCSP Stapling is disabled.
This will help you verify the status of OCSP Stapling on your website. If you see a “Not supported” message , check this Microsoft documentation for troubleshooting.
Conclusion
In conclusion, certificate revocation is a vital part of secure internet communication. Conventionally, addressing revocation was an absolute challenge. As cyber threats increase along with the growing number of devices, hackers find new techniques to compromise digital certificates.
Thus, real time validation provided by OCSP is more important than ever. By including a digitally signed response in the initial handshake, the server avoids the need for clients to query the CA’s OCSP responder, which reduces latency and potential privacy concerns thus helping in real time validation.
While no revocation method is a perfect one, OCSP Stapling continues to progress. New standards such as “must-staple” and “multi-stapling” are improving OCSP’s security standards. However, OCSP Stapling has significantly improved this process by making revocation reporting fast, efficient, and cost-effective. With industry-wide support for OCSP, all digital certificates can benefit from this.
How can Encryption Consulting help?
Encryption Consulting provides specialized PKIaaS solution with increased scalability and consistent support features. It’s a low risk managed solution that gives you complete control over your PKI without having to worry about the complexity of the system. Our services include configuration support, PKI monitoring, and cloud-based PKI service that manages the entire life cycle of certificates, delivers security, compliance, and operational efficiency. With extensive experience in the domain, we ensure the successful and secure implementation of OCSP stapling in your organization, tailored to your specific needs. By partnering with Encryption Consulting, organizations can unlock the full potential of, realizing tangible financial benefits while maintaining robust security measures.