How does the CA/B Forum Keep Code Signing Secure?
Have you ever wondered why some software is installed on your system without any warnings while others trigger an alert saying, “The software is not from a trusted source”? This isn’t random; it all comes down to code signing. It is a system designed to verify the legitimacy of the software you’re about to install. At the center of this is the CA/Browser Forum (CA/B Forum), which sets standards to keep that trust in place. Let’s explore how.
Code signing uses Public Key Infrastructure (PKI) to ensure that software is trustworthy. Developers sign their software with a private key, and a digital certificate from a trusted Certificate Authority (CA) verifies their identity. The certificate contains a public key that users’ systems use to check the software’s signature, confirming it hasn’t been tampered with. The CA/Browser Forum sets guidelines for trusted certificate authorities to issue these certificates, ensuring that only safe, verified software reaches users. This process protects users from installing malicious software.
What is the CA/B Forum Anyway?
The CA/Browser Forum (CA/B Forum) is a group that includes key players in the digital world, such as Certificate Authorities (CAs) like GlobalSign, Sectigo, Entrust, and DigiCert, as well as browser vendors like Google and Mozilla and operating system vendors like Microsoft and Apple. These organizations work together to define standards and best practices for the use of digital certificates, including those used in code signing.
The goal is to ensure the security and trustworthiness of software and websites so that users can be confident they are interacting with legitimate, verified sources. The CA/B Forum plays a crucial role in setting guidelines that govern how certificates are issued and managed, helping to keep the online world safe from threats like malware and fraud.
History and Purpose
Founded in 2005, the CA/B Forum initially focused on improving Extended Validation (EV) certificates to increase trust for website users. Over time, it expanded to cover all aspects of digital certificate management, including server certificates and code signing. The forum creates “Baseline Requirements,” which are guidelines for certificate authorities on how certificates should be issued and managed. These standards ensure consistency and security across the internet. Organizations join the Forum voluntarily to work together on creating industry standards for digital certificates, without any legal obligation. This voluntary group of certificate authorities and vendors of internet browsers, where even the suppliers of other applications that use X.509 digital certificates for TLS/SSL and code signing, are a part of the Forum.
The CA/Browser Forum’s Baseline Requirements (BRs) for Code Signing Certificates set strict rules for how Certificate Authorities (CAs) issue and manage code signing certificates. These requirements influence multiple security standards and regulations worldwide.
For example:
- NIST (National Institute of Standards and Technology) references BRs in its cryptographic guidelines (e.g., NIST SP 800-57 for key management and NIST SP 800-63 for digital identity). This ensures secure private key storage and signature verification.
- ETSI (European Telecommunications Standards Institute) aligns its EN 319 411-1/2 standards with BRs for trusted code signing certificates in Europe, ensuring compliance with eIDAS regulations.
- Microsoft, Apple, and Google require CAs to follow BRs for issuing Extended Validation (EV) Code Signing Certificates, ensuring software authenticity and integrity in their ecosystems.
- WebTrust for Code Signing audits verify if CAs comply with BRs before they can issue trusted certificates.
- ISO 21188 (Public Key Infrastructure) incorporates BR principles to standardize digital signature security across industries.
Because of these influences, BRs help create a consistent global standard for code signing, ensuring software publishers and end users can trust that signed applications and updates have not been tampered with.
Continuous Improvement of Code Signing Standards
To ensure that code signing practices remain secure, the CA/B Forum has consistently refined its Code Signing Baseline Requirements (CSBR) through various revisions. Since the initial adoption of version 1.2 in August 2019, each update has addressed emerging security threats and industry needs.
For example, the transition to RSA-3072 and SHA-2 timestamp tokens in 2020 (Version 2.1) was driven by the need for stronger cryptographic security. RSA-3072 was chosen because increasing computational power made smaller keys like RSA-2048 more vulnerable to attacks, ensuring long-term security. The adoption of SHA-2 timestamp tokens improved the reliability of signed code by providing stronger cryptographic integrity.
A major shift came in June 2022 (Version 3.0) with the adoption of the RFC 3647 framework, which standardized certificate policies and improved clarity in compliance requirements. More recent updates in 2023 and 2024, such as enhancements to private key protection and signing services, further strengthened the security posture of the code signing process. These updates help the industry stay ahead of security challenges, ensuring trusted and compliant solutions for developers and users.
For a full history of revisions and detailed changes, refer to the CA/B Forum Code Signing Requirements page.
Code Signing: The “Seal of Trust” for Software
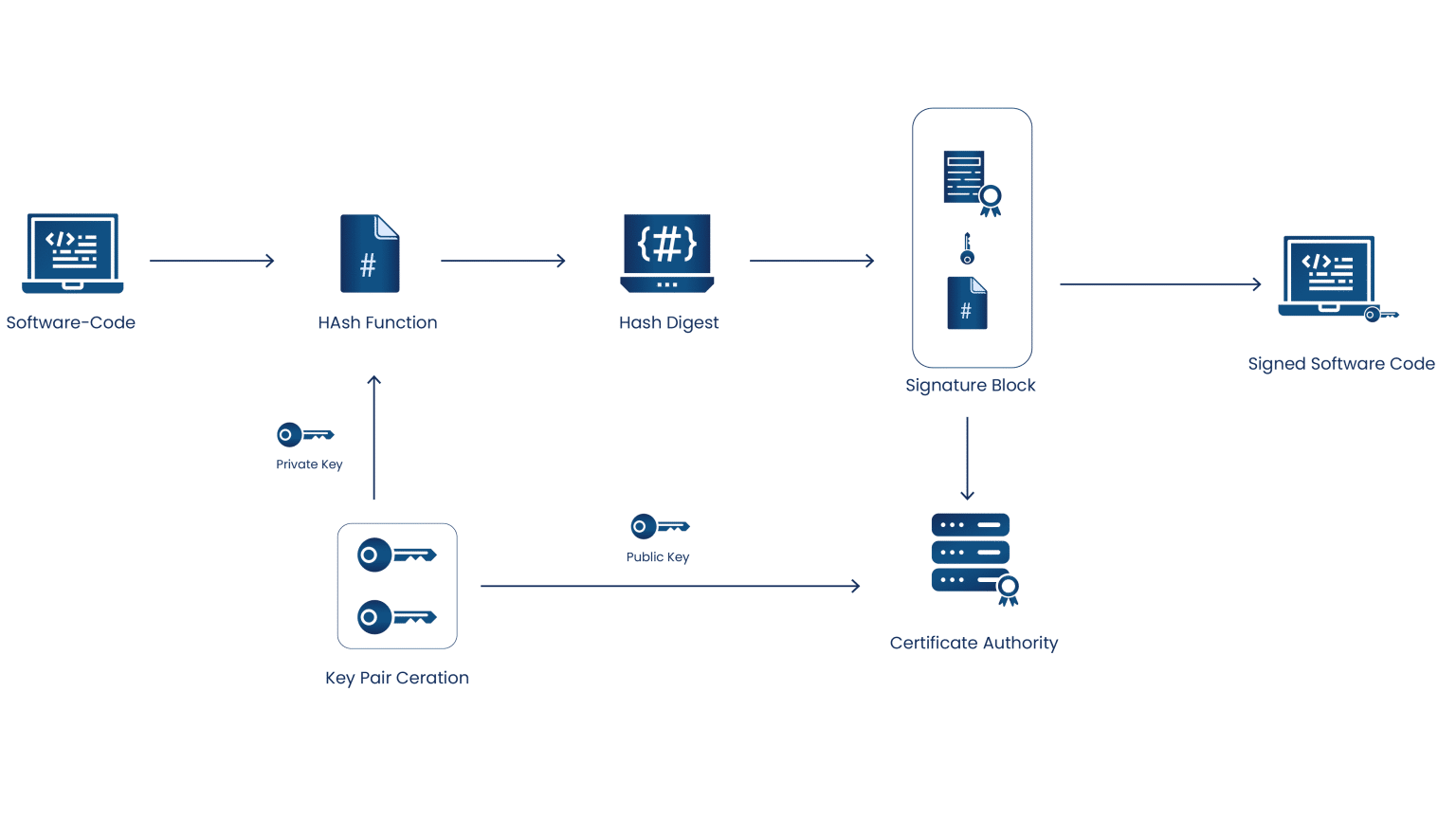
If you are wondering about what code signing is, think of it as the software equivalent of a signature on a legal document. When developers complete a piece of software, they use a code signing certificate to sign it digitally. This confirms that the software is authentic and comes from a verified source, ensuring it is recognized and trusted.
Certificate Authorities (CAs) are responsible for issuing these certificates, but not just anyone can distribute them. The CA/B Forum sets strict standards for how CAs should issue and manage code signing certificates, ensuring security and trust. If the software isn’t properly signed, your device may warn you that it could be risky. However, with a trusted certificate, the device allows you to proceed with confidence. A digital signature ensures both authenticity (verifying who signed the software) and integrity (ensuring the code hasn’t been altered after signing). Without code signing, hackers could easily disguise malware as legitimate software. To create these digital signatures, developers must obtain certificates from CAs that follow the Forum’s established guidelines.
How Does the CA/B Forum Ensure Compliance Using Certificate Authorities?
CAs are required to undergo regular audits conducted by independent third parties. These audits verify that the CAs are following the Forum’s standards and addressing any vulnerabilities in their systems.
CAs must undergo annual audits under frameworks like WebTrust for CAs or ETSI EN 319 411-1/2 to verify compliance with security standards. In case of security incidents, such as breaches or mis-issuance, CAs must report them immediately and take corrective action.
If a security incident occurs, like a security breach or a mis-issued certificate, CAs must report it immediately and take corrective action. This level of transparency and accountability helps build confidence in the security of digital certificates. Non-compliant CAs risk removal from trust stores like Mozilla’s or Microsoft’s, which can render their certificates untrusted. This level of transparency and accountability helps build confidence in the security of digital certificates.
The National Institute of Standards and Technology (NIST) also provides valuable guidelines on public key infrastructure (PKI), which align closely with the CA/B Forum’s standards. You can explore these guidelines on the NIST website.
How does the CA/B Forum set standards for Code Signing?
Let’s look at how the CA/B Forum impacts code signing standards:
-
Protecting Private Keys
In code signing, a developer uses a private key to create a “seal of trust” or digital signature. If a hacker gains access to this key, they could sign malicious software, making it appear legitimate. To prevent this, the CA/B Forum mandates that private keys must be securely stored, ideally on hardware security modules (HSMs) or cryptographic tokens.
Under the new CA/B Forum rules, key storage must comply with FIPS 140-2/3 standards, ensuring a higher level of security. Secure devices like HSMs are much harder to access than regular computers, making it significantly more difficult for hackers to steal private keys.
-
Strict Verification for Certificates
Before issuing a code signing certificate, a Certificate Authority (CA) must verify the identity of the developer or organization requesting it. This process follows guidelines set by the CA/B Forum and varies depending on the type of certificate—Organization Validation (OV) or Extended Validation (EV).
For both OV and EV code signing certificates, the CA verifies the legal existence of the organization by checking official government records or trusted business directories. It also confirms the physical address using reliable sources and performs phone validation by calling a publicly listed business phone number. Additionally, the CA ensures that the applicant has the authorization to request the certificate on behalf of the organization.
Additional verification steps apply to EV code signing certificates. The CA must confirm that the organization has been operational for a specific period, typically by reviewing business registration details. The applicant must also complete a face-to-face or equivalent identity verification process.
Once verified, the CA issues the code signing certificate, allowing the organization to sign software digitally. This helps operating systems and security tools confirm the authenticity of the software and prevents tampering or unauthorized modifications.
-
Revocation Rules
If a code signing certificate is compromised (say, a private key is stolen), it must be revoked immediately to prevent misuse. The CA/B Forum establishes specific guidelines for when and how Certificate Authorities (CAs) should revoke these certificates. According to the Baseline Requirements for the Issuance and Management of Code Signing Certificates, CAs must revoke a certificate within 24 hours if they detect unauthorized use or key compromise.
To enforce revocation, CAs maintain Certificate Authorities (CAs), maintain Certificate Revocation Lists (CRLs), and provide Online Certificate Status Protocol (OCSP) responses, enabling systems to verify whether a certificate is still valid before trusting signed software. However, OCSP stapling is preferred over CRLs because it is more efficient. CRLs require systems to download an entire list of revoked certificates, which can be slow and resource intensive. In contrast, OCSP stapling allows the server to provide a pre-validated OCSP response during the TLS handshake, reducing the need for real-time CA lookups and improving performance.
If a revoked certificate is used, operating systems and security mechanisms can block the software, preventing attackers from distributing malware under a trusted identity. These measures ensure that compromised certificates are quickly invalidated, maintaining trust in signed applications. For further details, you can refer to the CA/B Forum’s official Code-Signing-Baseline-Requirements.
Procedure for CA/B Forum’s Audits for Certificate Authorities and Code Signing
Before auditing, the CA/B Forum sets clear Baseline Requirements (BRs) for CAs. These guidelines cover everything from how certificates should be issued to how private keys are protected. For Code Signing Certificates, the Forum also sets standards to ensure that software is verified and safe to use.
Once the requirements are set, the auditing process starts. The auditing process for Certificate Authorities (CAs) starts with a pre-audit where the CA provides detailed information about its practices, like how it issues certificates and protects private keys. Then comes the on-site audit, where independent auditors check if the CA is following the CA/B Forum’s rules, like safeguarding keys and handling certificate revocations.
Sometimes, Penetration testing may also be done to find any weaknesses in the CA’s systems. If the CA does not follow the rules, it must fix the issues and could face penalties. Finally, follow-up audits are regularly conducted to ensure the CA continues to meet the required standards and remains secure. This process helps maintain trust in digital certificates.
For the code signing part, the CA must first verify the identity of software developers before issuing certificates. Then, auditors check the issuance process to make sure it follows proper security protocols. The CA also must monitor signed software to detect any unauthorized changes. If a certificate is compromised, the CA must revoke it immediately. This thorough auditing helps ensure the software is trustworthy and secure.
Through a thorough auditing process, the CA/B Forum ensures that Certificate Authorities (CAs) and developers issue Code Signing Certificates in compliance with strict security standards. These audits align with recognized compliance frameworks such as WebTrust for CAs and ETSI EN 319 411-1/2, which establish best practices for certificate issuance, key management, and revocation processes. WebTrust for CAs is widely adopted in North America, ensuring that CAs meet rigorous security and operational controls, while ETSI EN 319 411-1/2 defines similar requirements for European trust service providers. By adhering to these frameworks, CAs maintain the integrity of digital certificates, ensuring trust across the digital ecosystem. For more details, visit the CA/B Forum website.
New Requirements for Code Signing: What You Need to Know
The CA/B Forum has introduced some important changes to how code-signing certificates are issued, especially when it comes to protecting private keys. In the past, non-EV (Extended Validation) key pairs could be generated in software, which made it easy for the private key to be compromised. But now, things are a lot more secure!
To meet the new requirements, the key pair for both EV and non-EV code signing certificates must be generated and stored in a hardware security module (HSM). This module must meet or exceed FIPS 140-2 level 2 or Common Criteria EAL 4+ standards. What does this mean to you? The private key must be non-exportable, ensuring that it remains securely contained within the HSM and cannot be extracted or copied. With the private key locked down in hardware, unauthorized access or misuse becomes much more difficult, strengthening the overall security of the code-signing process.
Real-World Examples of the CA/B Forum’s Impact
To start with, a big-name software company’s private key was stolen. Without the CA/B Forum’s mandate to use hardware-backed key storage, attackers could push out malware disguised as legitimate updates. Thanks to these rules, such incidents are rare, as companies are encouraged (and often required) to use hardware-based security measures. According to the Forum’s guidelines, private keys must be generated and stored on secured hardware, such as an HSM or a trusted token. Additionally, Extended Validation (EV) Code Signing adds an extra layer of security by requiring stricter identity verification for organizations before issuing a certificate.
This includes verifying legal identity, operational existence, and phone validation. EV certificates also require mandatory hardware-based storage for private keys, ensuring they cannot be exported or misused. If the credentials are found to be tampered with or compromised, the certificates are revoked instantly, protecting the company’s security and integrity.
Another example is how operating systems and browsers use CA/B Forum-compliant certificates to determine which software is “safe.” If you try to install unsigned software, Windows Defender SmartScreen or macOS Gatekeeper may flag it with a warning, advising caution. Software signed with an EV Code Signing Certificate builds reputation faster with these security mechanisms, reducing unnecessary warnings and ensuring a smoother user experience while maintaining strong security protections.
How CodeSign Secure Ensures Full Compliance with CA/B Forum Guidelines?
Encryption Consulting’s CodeSign Secure makes the process of code-signing effortless and secure, ensuring full compliance with the CA/B Forum’s guidelines. We will now see how it works.
-
Streamlined Code Submission and Authentication: When you submit your code, CodeSign Secure authenticates and verifies its integrity to meet industry security standards. It ensures that your code meets the CA/B Forum’s strict security requirements from the very beginning, making sure your code is trusted and safe.
-
Key Protection with HSM Integration: Private keys are securely stored in hardware security modules (HSMs), fully adhering to the CA/B Forum’s key protection standards. This guarantees that your keys are protected from unauthorized access, keeping your code-signing process secure and compliant.
-
Seamless and Compliant Code Signing: CodeSign Secure signs your code using certificates that comply with the latest CA/B Forum Code Signing Baseline Requirements (CSBR). You can be confident that your code is signed to the highest industry standards, maintaining trust with your users and complying with security protocols.
-
Reliable Timestamping for Long-Term Validity: Timestamping your signed code ensures its validity even after certificates expire. CodeSign Secure automatically adds timestamps to your signed code, aligning with CA/B Forum guidelines and maintaining long-term trust in your software.
-
Automated Lifecycle and Revocation Management: With automated revocation handling and complete lifecycle management, CodeSign Secure ensures your signed code remains in compliance with ongoing updates to the CA/B Forum guidelines. This ensures long-term security for your code, with the flexibility to adapt to future changes in security requirements.
Why Should All This Matter to You?
For us, these standards make a difference each time we download software. Because the CA/B Forum sets the rules that CAs must follow, we can generally trust the certificates that come from them. A little question: What does this chain of trust depict, and what is its use?
Well, this chain of trust consists of root CAs, intermediate CAs, and end-entity certificates, ensuring that software from reputable sources is unlikely to harm your device. The root CA is the highest authority, trusted by operating systems and browsers. It issues certificates to intermediate CAs, which then validate and issue certificates to end entities, such as software publishers. Because each certificate is signed by a higher-trusted entity, this layered approach prevents unauthorized parties from issuing fraudulent certificates. As a result, bad actors have a harder time sneaking in, and users can trust that software signed with a valid certificate comes from a legitimate source.
How Encryption Consulting Can Help?
At Encryption Consulting, we help make code signing secure with solutions like Codesign Secure and Certificate Lifecycle Management, ensuring you stay compliant with the CA/B Forum guidelines. Our services help you manage your code signing certificates from start to finish, making sure they are properly issued, monitored, and revoked if needed.
We also provide PKI and HSM Services to protect your cryptographic keys. Using Hardware Security Modules (HSMs), we securely store your private keys and protect them from unauthorized access.
With these solutions, you can keep your software trusted, meet compliance standards, and reduce the risk of certificate compromise. For more details on secure code signing, visit our Education Center.
Enterprise Code-Signing Solution
Get One solution for all your software code-signing cryptographic needs with our code-signing solution.
Conclusion
The next time you install a program without any fuss, you can thank the CA/B Forum for ensuring strong protections, such as secure key storage, rigorous verification, and revocation protocols; they help the digital world run securely. It’s a little like the first line of defense for websites and software, keeping out the bad malware software so that we can all enjoy a better and safer digital experience.
To conclude what we discussed, the CA/B Forum’s role is to maintain trust, whether that’s for the websites you visit or the software you rely on. Their standards ensure that, as digital consumers, we have a layer of protection against the unknowns of the online world.