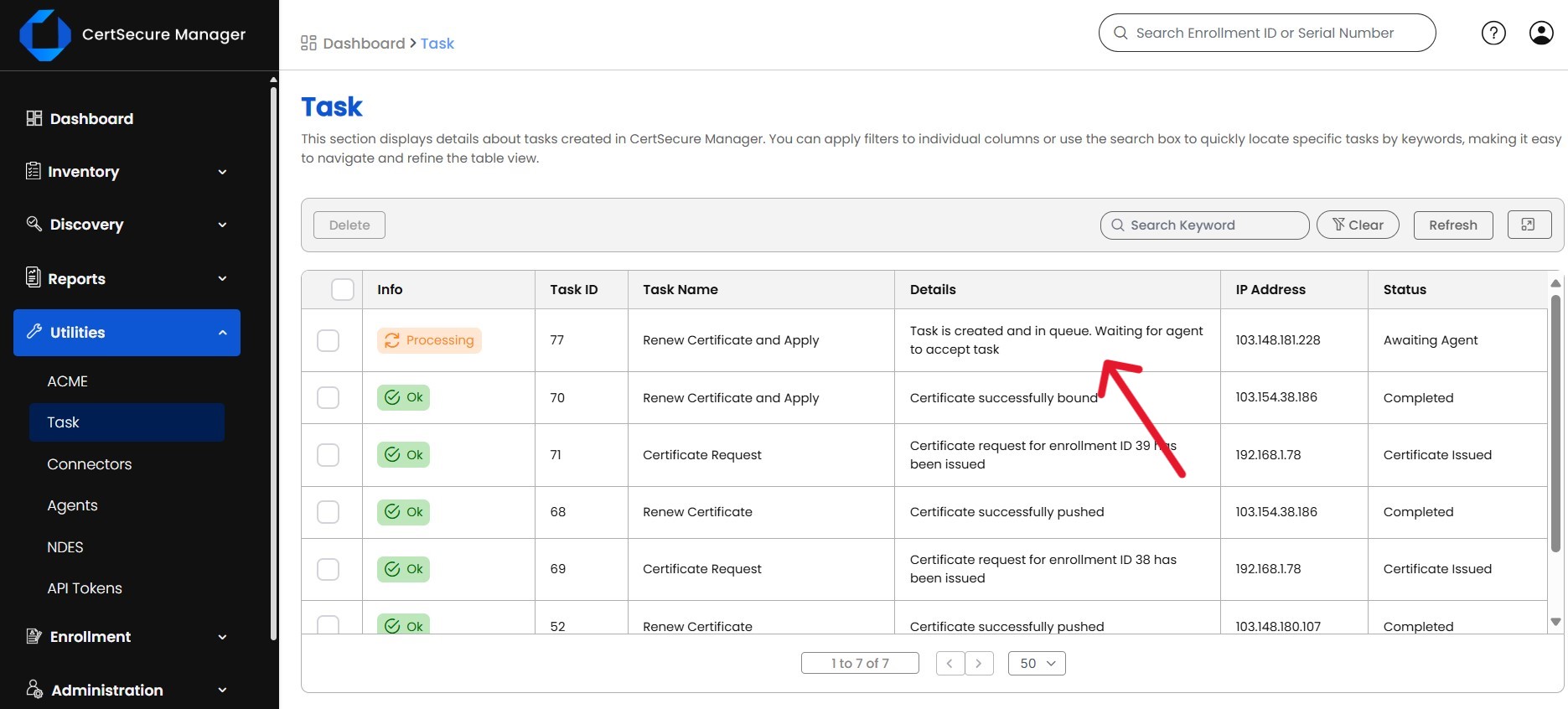
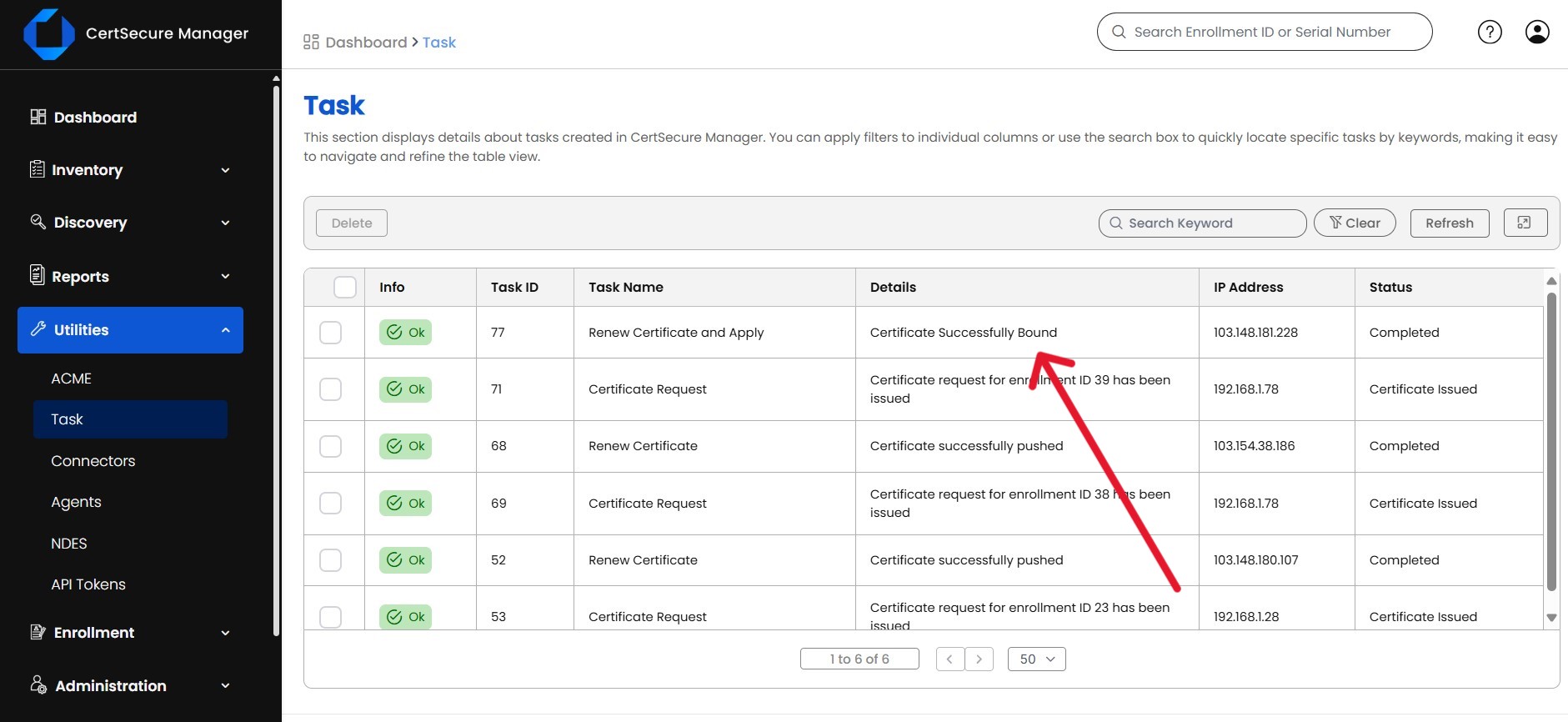
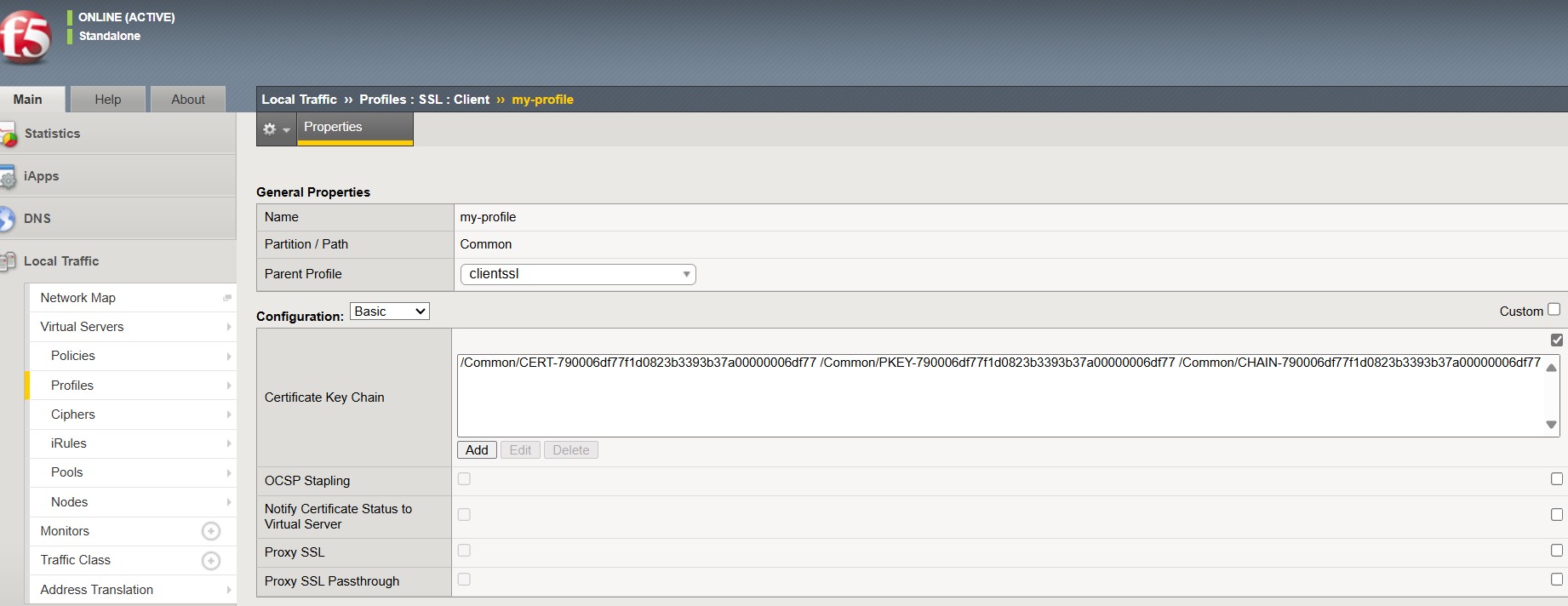
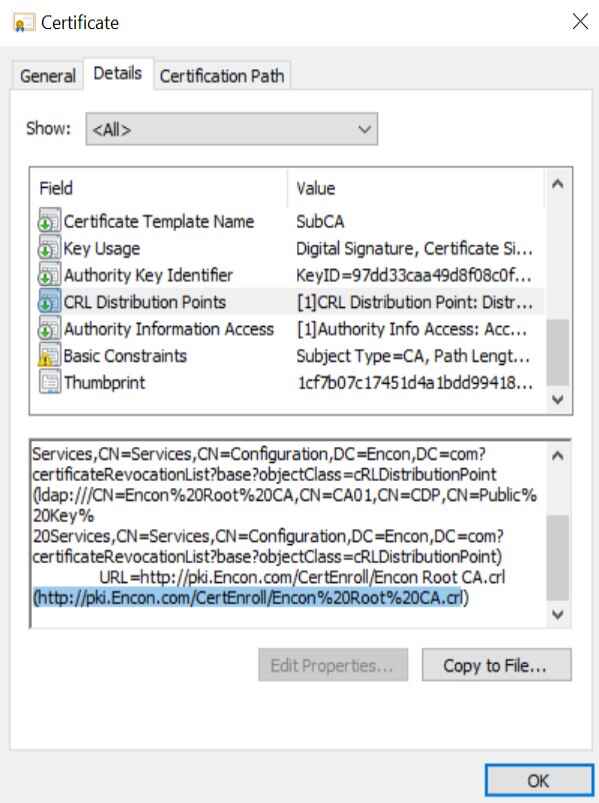
Securing software is extremely important in the interconnected world in which our industries operate. Every organization today needs to protect each and every piece of software inside their organization from rising digital threats and increasing incidents of software tampering.
This is where code signing comes into play. Code signing is the process of attaching a digital signature to software that confirms the source of the code and guarantees that this code hasn’t been tampered with after signing, which helps build trust. This security measure has become mandatory to maintain the integrity of software and build trust with users or customers.
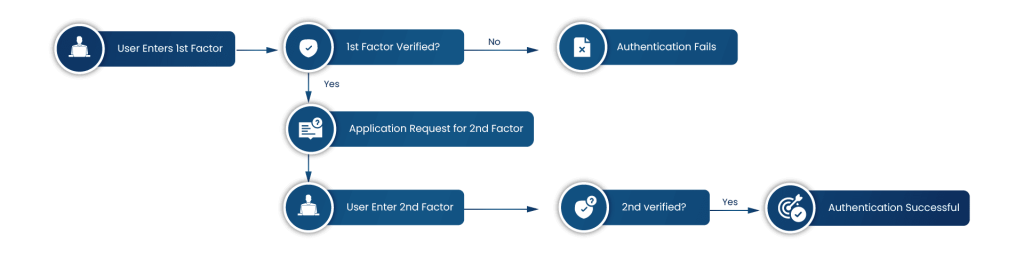
Now, let’s go over exactly what happens in the code signing process. A cryptographic hash is generated to attach the identity of the publisher to the software. This hash is encrypted with the publisher’s private key, and the users verify the authenticity of the software using the corresponding public key.
If this software had been tampered with after signing, the digital signature attached to it would break, which would alert users to potential issues. This process uses several key steps, adding more and more security by enhancing the integrity of the complete software distribution process.
How does Code Signing work
It’s important to understand each step to ensure the complete process works efficiently and effectively to meet all compliance requirements. These are the following core steps of code-signing:
-
Generating a cryptographic hash
A function that is used to generate a unique hash value of the software code. This hash acts as a digital fingerprint that is unique to your software.
-
Encrypting the hash
This hash is then encrypted using the publisher’s private key to create a digital signature. The signature, along with the public key, is included in the software package.
-
Distributing the software
The signed software, along with the digital signature, is distributed to the users or customers. The public key is also provided so the users can verify this signature to check the software’s authenticity.
-
Verifying the signature
When a user receives this software, their system uses the public key to decrypt the digital signature to obtain the original hash. Their system then generates a new hash of the software and compares it with the original hash.
Our code signing product, called CodeSign Secure, helps organizations like yours with the authenticity and integrity of software by effectively following the above process of secure code-signing. We support a client-side hashing technique, which benefits you by giving you faster and more secure data transfer to the server and then creating a unique digital fingerprint.
Later, a digital signature is generated using a FIPS 140-2 level 3 HSM on the server side, and this signature, along with the public key, is attached to the software package on the client side. Now, this signing operation can be done using signing tools like MS signtool Oracle’s JarSigner and by integrating with CI/CD pipelines like Jenkins, Azure DevOps, GitLab Cli, etc. Users can verify the software’s authenticity using the public key attached to the signature.
Compliance Regulatory Requirements
With digital threats becoming more and more sophisticated and supply chain attacks becoming increasingly common in the industry, stricter compliance requirements are being introduced by regulatory bodies worldwide to protect software integrity. These regulations and standards have made the use of code signing a mandatory security measure for maintaining software integrity and authenticity. Let’s look at these regulatory frameworks and how code signing contributes to these compliances.
Federal Information Processing Standards (FIPS)
In the United States of America, the National Institute of Standards and Technology (NIST) developed the FIPS compliance, which specifies the security requirements for cryptographic modules.
-
FIPS 140-2
This standard is mainly concerned with the security requirements for cryptographic modules within federal systems. It specifies the need for secure key management, integrity verification, and encryption algorithms.
-
Code Signing Applications: Software developers must use FIPS 140-2 compliant cryptographic modules for code signing to ensure that the digital signatures meet federal security standards. Our platform, CodeSign Secure, actively follows FIPS 140-2 compliance and uses the appropriate cryptographic module of Hardware Security Modules (HSMs) for storing the cryptographic keys inside it.
-
-
FIPS 186-4
This standard specifies the Digital Signature Algorithm (DSA) for generating and verifying digital signatures.
-
DSA in Code Signing: DSA for code signing ensures that the signatures are secure, reliable, and meet the federal requirements for software integrity. Our CodeSign Secure ensures the digital signature that has been attached meets these standards or not to build the trust chain.
-
General Data Protection Regulation (GDPR)
The General Data Protection Regulation is a very detailed data protection law approved by the European Union to protect the privacy and personal data of European citizens or of companies that want to operate out of Europe. Although GDPR focuses mainly on data protection, it is important to ensure the integrity and security of software that handles personal data.
-
Data Security
GDPR has made it mandatory for organizations to implement appropriate organizational and technical measures to secure personal data. This means that organizations need to prevent unauthorized access, accidental loss, or any kind of damage to the data. Our solution, CodeSign Secure, has a robust RBAC system that helps to ensure that only authorized developers can access the code signing portal, and we support AD authentication coupled with MFA to allow only authenticated users to onboard.
-
Software Integrity
Due to code signing, organizations can ensure that the applications handling personal data haven’t been tampered with. By signing software, organizations can ensure that the code is authentic. The digital signature generated by our CodeSign Secure addresses this issue so that the integrity of the software remains intact.
-
Compliance Demonstration
Using code signing as part of the data protection strategy can help organizations demonstrate compliance with GDPR’s security principles during audits and inspections.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA) sets strict standards for the protection of sensitive patient data in the healthcare industry.
-
Security Rule
HIPAA’s Security Rule mandates administrative, physical, and technical security to ensure the Confidentiality, Integrity, and Availability (CIA) of electronic protected health information (ePHI).
-
Code Signing Role: By signing healthcare software, organizations can ensure that applications that handle ePHI are secure and have not been tampered with, which also maintains data integrity. You can use our CodeSign Secure to digitally sign ePHI, as we have strong security measures incorporated into our server. No data can be tampered with, and confidential data always remains secure.
-
-
Compliance Assurance
Code Signing can be part of the technical security requirements by HIPAA. During compliance audits, organizations can demonstrate that their software applications are secure and meet the standards. Our CodeSign Secure has extensive logging and audit trails for detailed records of transactions that occur during the code signing process. This ensures that we take all the necessary steps to meet the HIPAA compliance.
Sarbanes-Oxley Act (SOX)
The Sarbanes-Oxley Act (SOX) was created to protect investors by improving the accuracy and reliability of corporate disclosures, mainly financial reporting.
-
Section 404
This section requires the management and auditors to establish and report on the internal controls over financial reporting (ICFR).
-
Software Integrity Controls: Code Signing can be used as a control mechanism to ensure that financial reporting software is secure and has not been altered, which helps in maintaining the integrity of financial data.
-
-
Audit Trail
Using code-signing, organizations can create a detailed audit trail for their software applications that demonstrates that robust controls over the software systems are created as required by SOX. We understand the importance of detailed audit trails and extensive logging and that’s why we ensure that this feature plays an important role for our clients to meet all necessary compliance requirements.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security (PCI DSS) sets security standards for organizations that handle credit card information to protect against data breaches and fraud.
-
Secure Software Development
PCI DSS requires organizations to follow secure software development practices to prevent vulnerabilities in payment applications.
-
Code Signing Requirement: By signing these payment applications, developers can ensure the authenticity of their software, thereby protecting it against malicious code insertion. Our CodeSign Secure only allows authorized personnel to perform code signing operations to make sure your information is always secure and can’t fall into the hands of inappropriate users.
-
-
Compliance Validation
During the PCI DSS compliance assessments, organizations can show that their payment applications are secure and meet the required standards by showing their code signing practices.
Implementing Code Signing Practices
Implementing code signing practices within an organization is extremely important to ensure the integrity and authenticity of the software. This involves several important steps that must be followed to achieve the highest levels of security. Below are the detailed guides for all the steps:
-
Obtaining a Code Signing Certificate
The first step to be implemented in code signing is to acquire a code signing certificate from a trusted Certificate Authority (CA). This certificate acts as a digital identity for the software publisher and is crucial for establishing trust with end-users.
-
Choosing a CA: We strongly recommend that organizations select a reputable CA that is widely recognized and trusted by operating systems and browsers.
-
Certificate Types: You should decide the type of certificate that is needed. Although standard code signing certificates are suitable for most applications, Extended Validation (EV) certificates offer enhanced security and fewer warnings to the end-users.
-
Issuance and Installation: Once the identity of the organization has been verified by the CA, they will issue the code signing certificate to the organization. This certificate must be installed on the system where the code signing will take place.
-
-
Integrating Code Signing into the Development Process
By integrating your code signing into the Software Development Lifecycle (SDLC), you can make sure that all the software builds have been signed before distribution. This integration helps you to maintain regular and consistent security practices throughout your development process.
-
Defining Policies: You need to establish clear policies and procedures for code signing within the development team. This includes which types of software and files will be signed and who will have the authority to sign the code, like a robust RBAC (Role Based Access Control).
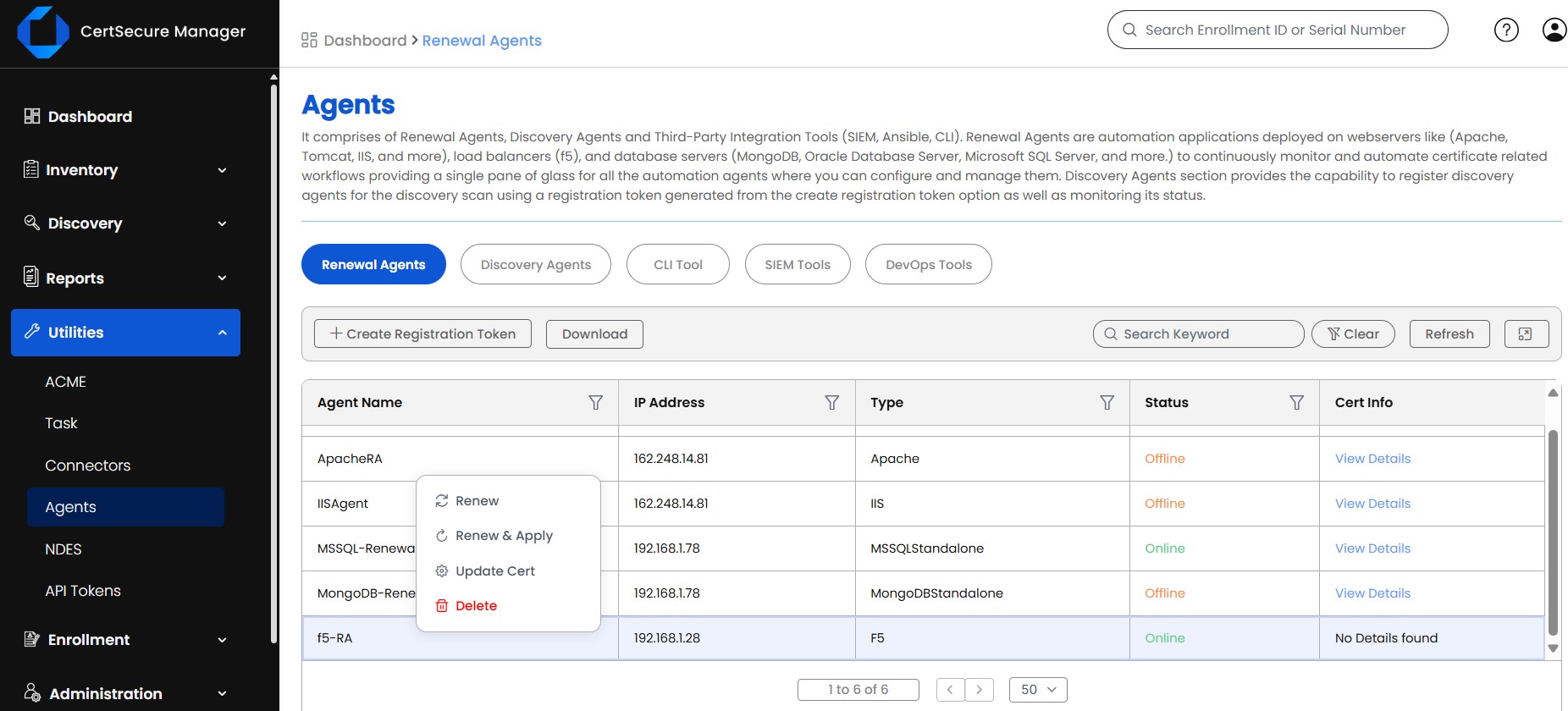
Our CodeSign Secure has a robust RBAC in which we have separate roles defined with specific permissions to perform code signing operations. This will help your organization to keep track of who signs and what they sign.
-
Development Tools Integration: Integrate code signing into your development tools and environment to automatically sign code during the build process, like Jenkins, Azure DevOps, GitLab, and so on. Our CodeSign Secure supports all the different CI/CD pipelines to automate the code signing process. This not only saves you time but also makes the process less prone to human errors.
-
Version Control Systems: You need to ensure that code signing is properly integrated with your version control system (VCS) like GitHub. This helps maintain a history of signed code versions and allows for tracking changes and updates. Our CodeSign Secure supports a build verification feature integrated with GitHub to ensure the code we support in the server is not malicious, and this step helps us avoid one of the most famous cyber security attacks – Solaris attacks.
-
-
Securing the Private Key
The private key used for code signing must be stored securely to prevent unauthorized access to it. If this private key is compromised, it can lead to attackers tampering and then signing code, which in turn undermines the trust in the software.
-
Hardware Security Modules (HSMs): Organizations should use HSMs to store private keys securely. HSMs are physical devices designed to safeguard private keys and perform cryptographic operations in a secure environment. The private keys are stored in a FIPS 140-2 Level 3 HSM in our CodeSign Secure. We ensure the private key doesn’t leave the HSM at any cost, which makes it less prone to tampering.
-
Access Controls: You should restrict access to the private keys to authorized personnel only. It is a good approach to implement RBAC and multi-factor authentication (MFA) to enhance security.
-
Key Rotation and Revocation: You should periodically rotate private keys to reduce the risk of compromise. Also, a backup plan should be in place for revoking and replacing keys in case of a security breach.
-
-
Automating Code Signing Process
By automating code signing processes, you can streamline operations, reduce the risk of human error and ensure consistency. This process is generally important for organizations with frequent software releases.
-
Continuous Integration/Continuous Development (CI/CD): Integrate code signing into your CI/CD pipelines. Tools like Jenkins, GitLab, Azure DevOps, and so on allow for automated code signing as part of the build and development process.
-
Scheduled Tasks: Set up scheduled tasks to sign code automatically at specific intervals or upon certain events.
-
-
Testing Signed Code
Before releasing this signed code, thorough testing is important to ensure that the signing process does not introduce any issues and the code behaves in the desired outcome.
-
Functional Testing: Verify that the signed code functions correctly and that no errors are introduced during the signing process.
-
Signature Validation: Test the signature verification process on different platforms and environments to ensure compatibility and that the signature is trusted.
-
User Acceptance Training (UAT): Perform UAT to ensure that the end-users are able to successfully install and run the signed software without facing any security warnings or issues.
-
Best Practices for Code Signing
To maximize the benefits of code signing and ensure the security and integrity of software, organizations should stick to the following best practices:
-
Use Strong Cryptographic Algorithms
-
Modern Algorithms: We suggest you utilize only modern cryptographic algorithms such as SHA-256 for hashing and RSA or ECC for encryption. These algorithms provide strong security against the latest threats. Our CodeSign Secure supports only the latest algorithms for key generation and hashing methods.
-
Avoid Outdated Algorithms: You should refrain from using outdated algorithms like SHA-1 or MD5, which are susceptible to collision attacks and other vulnerabilities.
-
Regular updates: Your organization and developers should stay updated with the latest recommendations from cryptographic communities and standard organizations to ensure your algorithms remain secure.
-
-
Implement Time Stamping
-
Validity Extension: Time stamping ensures that the digital signature remains valid even after the code signing certificate expires. This is essential for maintaining long-term software authenticity. So, we at Encryption Consulting suggest you use only the trusted time-stamping servers when performing the code signing operations.
-
Trusted Time-Stamping Authorities (TSAs): You should use timestamps from trusted TSAs to ensure the integrity and authenticity of the time stamps themselves. Our code signing process only works with the most trusted and industry-specialized time-stamping authorities during signature packaging time.
-
Regulatory Compliance: Many regulatory frameworks require time stamping to demonstrate when the software was signed, ensuring compliance with legal and industry standards.
-
-
Regularly Rotate Keys
-
Key Rotation Policies: Your organization needs to establish and enforce key rotation policies to minimize the risk of key compromise. Regularly rotating keys ensures that even if a key is compromised, its impact is less.
-
Automatic Key Rotation: Automated systems are used to handle key rotation, reducing the risk of human error and ensuring timely updates. Our CodeSign Secure has the features of auto key-renewal and key-rotation policies during key generation. This way, we ensure that automated processes are followed, but this feature is optional, so the user can decide whichever option they want to opt for.
-
Secure Key Storage: We encourage the developers to store keys securely using Hardware Security Modules (HSMs) or other secure key management systems to protect them from unauthorized access.
-
-
Monitor and Audit Signed Code
-
Continuous Monitoring: You should implement continuous monitoring systems to track the integrity of signed code. This helps identify unauthorized modifications or tampering.
-
Logging and Alerts: Developers should set up logging mechanisms to record all code signing activities. Configure alerting systems to notify security teams of any anomalies or suspicious activities. Our CodeSign Secure has an extensive logging system, which helps in tracking all the code signing activities.
-
Regular Audits: Your organization should conduct regular audits of signed code to ensure compliance with security policies and identify potential vulnerabilities or unauthorized changes.
-
Common Challenges and Solutions
While code-signing offers a lot of benefits, there are still a lot of challenges that can arise. Understanding these challenges makes solving them simpler and can help maintain the integrity and security of software. We will take you through some of the most common challenges and give you effective solutions:
Key Management
ChallengeIt is a very critical task to secure and manage the private keys used for code signing operations. If a private key is compromised, it can lead to the unauthorized signing of malicious code and undermine the trust in software.
Solutions-
Hardware Security Modules (HSMs)
Using HSMs can help in securely storing private keys. HSMs provide physical protection to ensure that the keys are used only in a secure environment.
-
Secure Key Management Systems
Implementing key management systems offers features such as key generation, rotation, storage, and destruction in a secure manner.
-
Access Controls
Access to the private keys should be restricted using strict role-based access controls (RBAC) and multi-factor authentication (MFA). Only authorized personnel should have access to key management systems.
-
Regular Key Rotation
It is a good approach to frequently rotate keys to decrease the impact of potential key compromise. Organizations should automate the process of key rotation to minimize the risk of human error.
-
Backup and Recovery
Organizations should maintain secure backups of the private keys and should implement recovery procedures to handle key loss without any security corruption.
Scalability
ChallengeAs your organization scales, the number of software needed and developed will also increase, making your manual code signing a time-consuming and impractical process.
Solutions-
Automation Tools
We recommend utilizing automation tools to streamline the code-signing process so as your organization grows, your code-signing practices can grow alongside it. You have to integrate your code signing solution into the Continuous Integration/Continuous Deployment (CI/CD) pipelines to automate the signing of every build.
-
Centralized Singing server
You need to implement a centralized signing server that can manage multiple requests from various development teams, which in turn will increase efficiency and ensure consistency in the signing process.
Compliance and Auditing
ChallengeIt is quite challenging to ensure compliance with regulatory requirements and maintain detailed audit logs, especially in complex development environments.
Solutions-
Compliance Frameworks
Your organization needs to follow established standards and compliance frameworks relevant to your industry, like – GDPR, HIPAA, SOX, and PCI DSS. Your developers need to implement policies and procedures that align with these frameworks.
-
Strong Auditing Mechanism
Organizations need to implement strong auditing mechanisms to log and track all code signing operations. You should use logging systems to record detailed information about who signed what code and when.
-
Reporting and Documentation
Developers should maintain documentation and regularly generate reports on all the code signing operations and compliance status. This helps in demonstrating compliance during external audits and inspections.
Revocation of Certificates
ChallengeIf a security breach happens, it is very important to revoke compromised certificates to prevent the distribution of malicious code. However, managing revocation and reissuing certificates can be challenging.
Solutions-
Certificate Revocation Plan
Organizations need to develop clear plans or policies for certificate revocation, which will include procedures for identifying compromised certificates, notifying stakeholders, and revoking the certificates.
-
Rapid Re-Issuance
You need to ensure that the Certificate Authority (CA) can expedite the re-issuance of a new certificate in case of a breach.
How Encryption Consulting Can Help
Encryption Consulting will help your organization with our expertise in encryption, key management, and regulatory compliance; we also offer services that will help design your code signing strategy. Our product – CodeSign Secure is developed to help streamline and secure your code signing process.
-
Assessment and Strategy Development
We assess your current code signing practices and help in developing strategies to address your specific needs and compliance requirements.
-
Key Management Solutions
At Encryption Consulting, we believe it is very important to protect your private key. We provide key management solutions that include HSM-as-a-service and guides on key storage practices.
-
Training and Education
We ensure that your developers understand the importance of code signing and follow the best practices. We provide comprehensive training programs for your organization and security teams.
-
Implementation Services
We provide end-to-end implementation support for integrating code signing into your build pipelines.
Conclusion
To conclude, code signing is a critical component of your organization’s security. It helps you to build trust among your users by ensuring the authenticity and integrity of software to prevent tampering. Our CodeSign Secure is developed by keeping all your security needs and compliance requirements in mind to offer you a solution that is both user-friendly and keeps all preventative measures in place to ensure that your software remains secure, compliant, and trusted round the clock.
Our advanced features not only protect your organization from tampering and malicious code alterations but also ensure that your software remains compliant with all regulatory requirements and builds trust with users. So, trust us to help you protect your software, build user confidence, and deal with the complexities of regulatory compliance with CodeSign Secure.