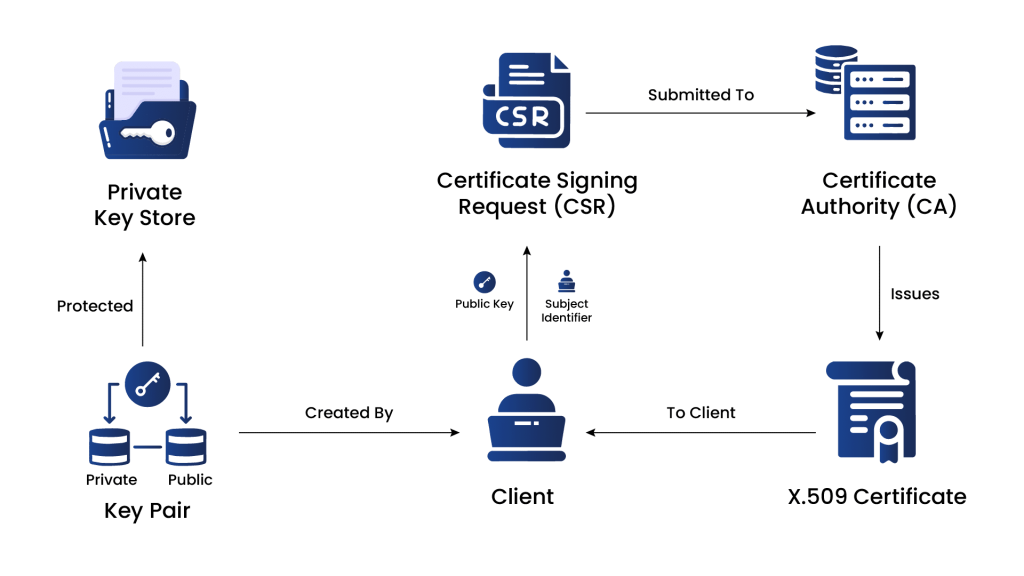
In the beginning, let us first understand what a CSR is. A Certificate Signing Request (CSR) is a request you make to a Certificate Authority (CA) to issue a digital certificate. Typically, it is a block of encoded text that includes details such as the organization’s name, domain name, country, and public key, which the CA uses to create a certificate for you. It is crucial in the certificate lifecycle since it marks the initial step in creating a certificate.
This request additionally acts as a method to confirm the website owner’s identity and domain ownership, thereby assuring users that they can trust the site with their information. This process is very important to prevent users from mistrusting the website and believing their data is not safe.
A CSR is not just a request for a certificate; it contains important information about your organization and its domain, which is used by the Certificate Authority (CA) to verify your identity. One common question that often comes up when managing certificates is: Do we have to generate a new CSR to get our certificate renewed? The answer is not straightforward; it depends on various factors. Sometimes, reusing a CSR leads to carrying over outdated or incorrect details, whereas in other cases, it is totally acceptable.
This blog explains when and why it is important to generate a new CSR, the risks of reusing an old one, and the key best practices to follow for a smooth and secure renewal process.
When can we use an existing CSR?
Even though this is generally discouraged, there are still a few possible cases where we can use an existing Certificate Signing Request. However, such a step should be taken carefully as it has potential limitations and security risks.
-
CA Guidelines on Existing CSRs
If the corresponding private key is secure, some Certificate Authorities may permit the use of existing CSRs. However, not all CAs have the same policies; thus, checking with your CA to learn its specific requirements is worthwhile.
-
Short Renewal Periods
If the renewal takes place soon after the certificate has been issued, such as within a few days or months, and your organization’s details, domain, or security measures remain unchanged. This is particularly useful for urgent renewals.
-
Uniformity Across Systems
The reuse of CSR can promote uniformity across systems, reducing the risk of incorrect configurations. It also ensures smooth operations and minimizes downtime caused by mistakes, which is very important for the smooth functioning of high-availability situations.
-
Internal Testing and Development Environments
CSR reuse may be an efficient option for non-public or internal environments, such as development or testing systems. Since these environments are usually at lower risk, generating a new CSR for each renewal may be less critical.
-
Low-Risk Domains
For simple sites that do not handle sensitive information, generating a fresh CSR may not be strictly necessary. These domains typically have lower security requirements, making it feasible to reuse an existing CSR without significant risk.
Potential Risks of Reusing an Old CSR
On the surface, reusing an old Certificate Signing Request may appear to be an easy option; however, it has multiple risks and disadvantages that stand out. Some of the reasons why it is more advisable to use a new CSR for every renewal are:
-
Risk of Reusing Keys
If you decide to reuse an existing CSR, you will also have to reuse the private key. While this is convenient, it is generally discouraged due to security concerns. Security issues arise when such compromised keys are in use, as they may create dangerous opportunities and vulnerabilities for your site. For example, if the key is outdated, stolen, or exposed, it could leave the site vulnerable to attacks such as Man-in-the-Middle (MITM) attacks, Brute Force attacks, and Cryptanalysis attacks.
Furthermore, private keys generated with older encryption standards may not be strong enough to protect against modern threats. This could allow attackers to exploit vulnerabilities in outdated cryptographic algorithms, putting the security of both the certificate and the data it protects at risk.
-
Limited Security Improvements
Certificate renewals offer a chance to enhance security with the latest cryptographic standards of asymmetric encryption. Using an outdated CSR may hinder your progress, possibly exposing your site to risks that could be mitigated using modern technology.
-
Regulatory Constraint
Certain regulatory or industry standards sometimes enforce key rotation policies. Using an old CSR may violate some of these policies, especially in industries that follow high compliance standards, such as finance, healthcare, and government institutions.
-
Potential Expiration of Associated Details
A CSR typically includes information about the organization and its domain, which may become outdated over time. So, if your organization’s information is inaccurate due to the use of an outdated CSR, it can create complications with renewal and might even cause the respective CA’s refusal.
-
Incompatibility with CA Updates or Protocols
CAs periodically adjust their validation standards, encryption policies, and various other procedures. An older CSR might require increased coordination with these changes, resulting in challenges during the renewal process, which may, in turn, cause delays or refusals in the issuance of the certificate.
In short, while there may be scenarios where reusing a CSR is permissible, it is considered a best practice to generate a new one for every certificate renewal. This way, you can minimize risks and make sure that your system is up to date in terms of security and has active support for the regulations, standards, and protocols. Taking this proactive approach helps secure your site, your users, and your organization from potential vulnerabilities and complications.
When is it appropriate to create a new CSR for renewal?
Renewing a certificate means terminating an existing certificate and issuing a new one to enhance your website’s security. In most situations, creating a new Certificate Signing Request for every renewal is highly advisable, as it guarantees your certificate complies with the latest security protocols and reduces possible risks. These are the cases when it is especially critical to take the time and effort to prepare a fresh CSR:
-
Revised Organizational Details
The organization’s details may change over the years. Instances of such modifications involve the change in the domain name or any additional details that are present on the CSR. Therefore, a new CSR should be created to integrate this latest information to ensure that the certificate stays current.
-
Security Issues
Whenever you renew your certificate, a new CSR must be created each time. This is due to the fact that the encryption techniques and hashing methods utilized may have advanced and might surpass those employed earlier. Some hosts may allow the old CSR to be used. However, it is preferable and more secure to create a fresh CSR, utilizing modern, enhanced encryption and hashing technologies, reducing security risks and keeping the site protected against evolving threats.
-
Advantages of Utilizing New Key Pairs
While the existing private key may suffice in certain situations, creating a new key pair along with a corresponding CSR is highly recommended. New keys lower the chances of compromise and the risk of exposing older keys, which might be more susceptible to attacks.
-
Regulatory Compliance
In sectors with strict regulations, like healthcare, finance, or government, frequent key rotation is typically necessary for adherence to compliance standards. Many regulations mandate that new CSR and key pairs must be obtained whenever a certificate is renewed as one of the security practices for the organization.
-
Changes in the Policy of CA or the Industry
In case your CA or the industry you belong to has changed any policies or protocols, a new CSR must be generated to satisfy the new conditions. This can include requirements for stronger encryption algorithms or updated validation processes.
-
Extended Certificate Lifespan or Long-Term Use
When renewing certificates that are expected to be in use for a longer duration, such as 12 months or more, generating a new CSR is the best practice. Using a new key pair reduces the risk of vulnerabilities that can accumulate over time with older keys.
-
Adopting New Cryptographic Standards
When you plan to switch to a more robust key type or a better hashing algorithm, such as moving from RSA to ECC, a new CSR must be generated. This enables you to improve your website’s security using modern encryption standards.
Therefore, creating a new CSR for each renewal is considered the best security practice as it reduces risks, guarantees compliance, and aligns with changing CA and industry standards.
How can Encryption Consulting help?
Encryption Consulting provides a complete Certificate Lifecycle Management solution, including CertSecure Manager, which aims to optimize the entire certificate management process. It encompasses the end-to-end process from first discovery and inventory control to issuance, deployment, maintenance, and extensive reporting. It handles everything for you, from creating the CSR and filling in the details to sending the request straight to the Certificate Authority (CA).
By automating the renewal process, you can focus on more important tasks while reducing the risk of errors that often come with manual work. It makes complex tasks easy with smart report generation, alerting, and automation. Moreover, the solution enables secure and efficient certificate processing by facilitating automatic installation on servers and automatic certificate enrollment. Overall, it is a smart and flexible solution that enables organizations to manage the issuance of secure and current certificates conveniently.
Conclusion
To sum up, although there is a possibility to reuse a previous CSR while renewing a certificate, the wisest and most secure way is to create a new Certificate Signing Request. Renewing your SSL/TLS certificate is more than just routine maintenance; it is an opportunity to strengthen your website’s security. Creating a fresh CSR ensures the certificate incorporates updated information, complies with regulations, and reduces vulnerabilities.
Whether you do everything manually, including issuing and renewing certificates, or have special certificate management software, controlling the entire renewal process will guarantee that your site is safe and reliable. Do not leave it to the last minute; be proactive and keep your certificates up to date!