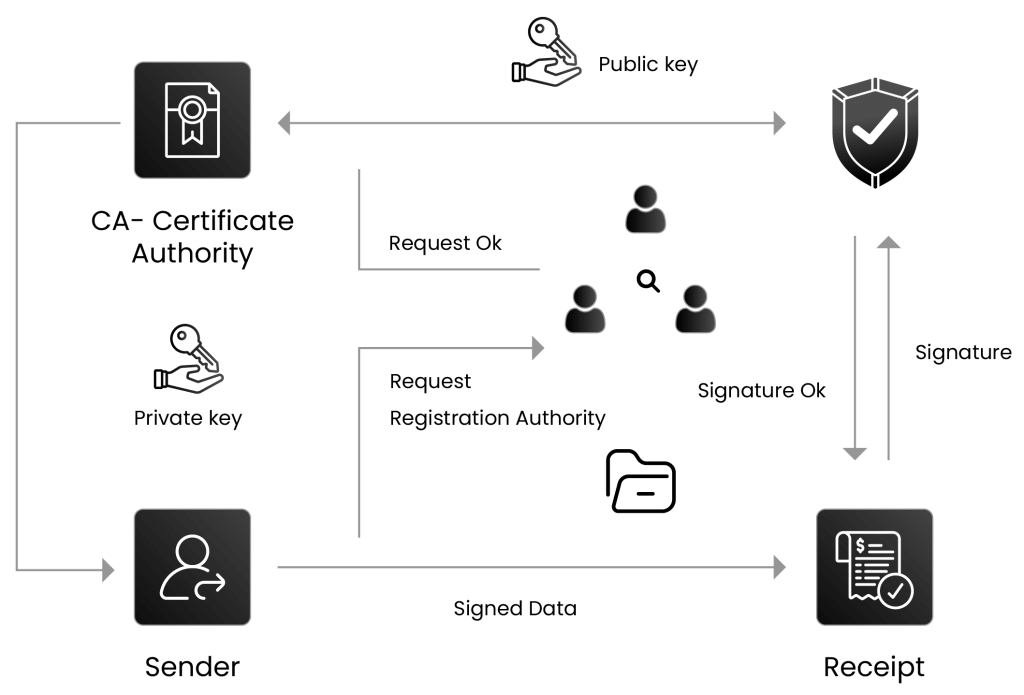
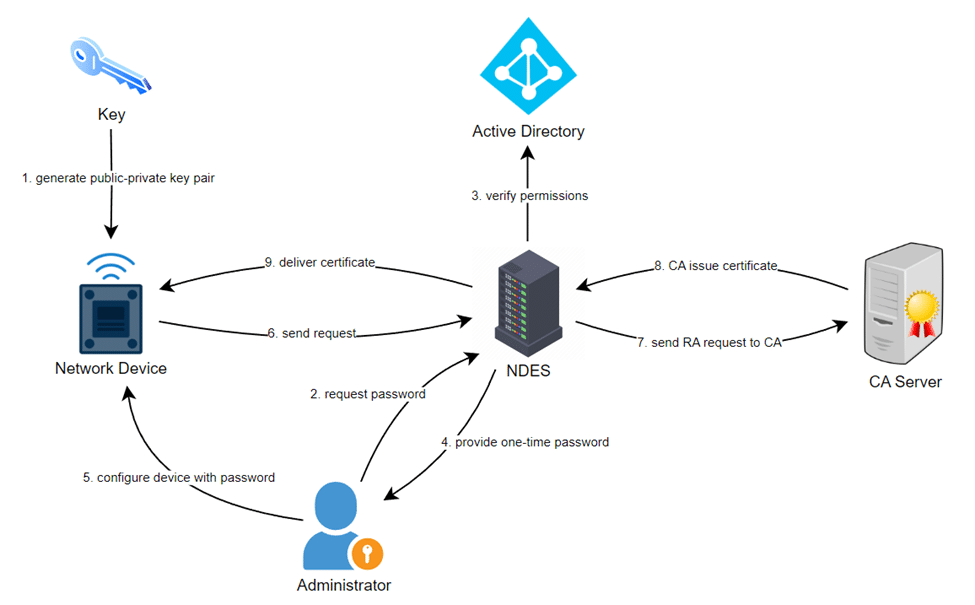
In today’s software development era, security standards are given top priority to ensure the protection of applications. Organizations are focused on implementing better security solutions to safeguard communications, authenticate users and maintain data integrity.
However, legacy PKI systems, the foundation of digital security, come with several disadvantages compared to modern PKI systems. These traditional systems often lack the flexibility, scalability and automation required to meet the evolving demands of modern enterprises. Modern PKI addresses these shortcomings by offering enhanced security, better cloud integration and improved scalability, making it the preferred choice for organizations to stand against cyber threats.
Over the last decade, PKI has proven to be a foundation of cybersecurity, where various reputed organizations have used it to secure their products. Nowadays, Passwords can be easily compromised through phishing, brute-force attacks, or database breaches, especially if users create weak or reused passwords. Email IDs are often publicly known or guessable, which serves as a single-entry point, increasing vulnerability. Moreover, passwords are prone to human error, such as forgetting or mishandling.
Therefore, PKI has surpassed the negatives of using email IDs and passwords for security purposes by enabling secure communication through digital certificates, which verify the identity of users or systems, mitigating phishing and credential theft risks and has become a trustable solution to many organizations.
There is a misconception that Legacy PKI is cost-effective, but the reality is legacy PKI comes with a long list of hidden costs. We will be looking into these unanticipated costs that legacy PKI offers.
First, let us gain some knowledge about Legacy PKI.
What is Legacy PKI?
Legacy Public Key Infrastructure (PKI) refers to an outdated or older implementation of PKI systems for managing digital certificates and cryptographic keys. These systems were typically designed and deployed using the technologies, standards and processes available at a particular time.
The rigidity of legacy PKI arises from factors such as dependence on outdated cryptographic algorithms, static architectures and limited support for automation and scalability. These systems often struggle to integrate with modern frameworks like cloud environments, DevOps pipelines and IoT ecosystems, which demand dynamic and scalable security solutions.
Key challenges of legacy PKI include the complexity of deployment and management, difficulties in scaling for large or diverse user bases, and manual certificate handling that leads to errors, inefficiencies and vulnerabilities due to outdated algorithms.
Some of the real-life scenarios where Legacy PKI is in use include:
Banking Token Authentication
Bank uses PKI to secure online banking with hardware tokens that generated PKI-based authentication keys. For example, Early implementations by banks like HSBC or Barclays involved issuing physical tokens to customers for secure two-factor authentication (2FA).
These tokens generated PKI-based authentication keys, providing enhanced security at the time. However, they represent legacy PKI due to their reliance on static, hardware-based solutions that lacked scalability and flexibility.
Specific challenges include the high cost and logistical complexity of distributing and maintaining physical tokens for large customer bases. These systems also lacked adaptability to modern digital banking channels, such as mobile and online platforms, which demand software-based, user-friendly authentication methods.
Furthermore, the dependency on hardware introduced usability challenges, as tokens could be lost or damaged, disrupting customer access. The lack of integration with newer technologies, automation and real-time monitoring further limited their utility, making them unsuitable for the fast-evolving needs of modern banking systems.
VPN Authentication
Many enterprises utilized PKI for Virtual Private Network (VPN) authentication in the early 2000s to secure remote access for employees. For example, Cisco AnyConnect VPNs often relied on digital certificates issued by internal PKI to authenticate users securely.
However, these setups are now considered legacy due to several challenges. Managing certificates was often manual and time-consuming, leading to errors like expired certificates. Scaling was difficult as workforces grew and the systems couldn’t easily adapt to modern needs like cloud integration or hybrid work setups. Outdated protocols and limited automation further reduced their effectiveness, making them unsuitable for today’s dynamic security requirements.
Negatives of Legacy PKI
PKI is a foundational technology that enables secure communication, authentication and data integrity by leveraging encryption and digital certificates. However, as technology evolves, Legacy PKI can become inefficient, insecure and difficult to maintain. Here are some negatives of using Legacy PKI:
Outdated Encryption Standards
Legacy PKI often uses older algorithms (e.g., SHA-1 or RSA with small key sizes) that may no longer meet modern security standards, making them vulnerable to attacks.
SHA-1 is particularly risky because it is prone to collision attacks, where two different inputs can produce the same hash value. SHA-1 has not been considered secure since 2005. Moreover, NIST formally deprecated the use of SHA-1 in 2011 and declared that it should be phased out by 2030.
Static Infrastructure
Older PKI systems were typically built for static, predictable setups, such as internal enterprise networks, where the number of devices and users was relatively stable and limited. This architecture lacks the scalability required for modern needs like IoT, cloud integrations, or dynamic digital environments.
For example, consider an IoT deployment with thousands of devices needing unique digital certificates for authentication. A legacy PKI system may struggle to handle the volume due to manual certificate issuance, renewal and revocation processes.
Additionally, it might lack the ability to automate certificate management in IoT platforms. This could lead to operational inefficiencies, increased risk of expired or misconfigured certificates and delays in deploying or securing new devices. In contrast, modern PKI solutions provide dynamic scalability and automation, ensuring the latest security without overburdening administrative resources.
Manual Certificate Management
Legacy systems typically depend on manual processes for issuing, renewing, revoking and tracking digital certificates, which introduces several challenges and risks. These manual workflows are labor-intensive, requiring administrators to handle tasks individually for each certificate. This not only increases operational overhead but also leaves room for human errors, such as issuing certificates with incorrect configurations or failing to renew them before expiration.
For example, in an organization with hundreds of applications and devices, an administrator might overlook renewing a critical certificate before its expiration. If that certificate expires unnoticed, it could cause a system outage, disrupt services or block user access. Additionally, if a compromised certificate is not promptly revoked, attackers could exploit it to impersonate legitimate systems or intercept sensitive communications.
Security Vulnerabilities
Legacy PKI systems are prone to security vulnerabilities due to their outdated architecture. One of the major issues is that they are often unpatched, leaving them exposed to known vulnerabilities. As discussed above in the article, many legacy PKI systems rely on older cryptographic algorithms like SHA-1 or RSA with small key sizes, which have been proven insecure. For example, an attacker could use the weaknesses in SHA-1 to forge digital certificates, leading to man-in-the-middle (MITM) attacks, where attackers intercept and manipulate communication between two users without their knowledge.
Another major vulnerability is the absence of modern security features like multi-factor authentication (MFA). Legacy PKI systems often rely on passwords to secure administrative access. This makes them highly vulnerable to credential theft, brute-force attacks and phishing. For example, if an attacker gains access to the PKI system’s administration panel using stolen credentials, they could issue fake certificates, revoke original ones or compromise the entire trust chain causing damage to the organization.
Apart from these vulnerabilities, legacy PKI systems lack advanced features like certificate pinning and real-time monitoring. Certificate pinning ensures that only a preapproved certificate can be used to secure a connection, which helps prevent attackers from using fake certificates issued by compromised certificate authorities (CAs). Without pinning, an attacker could exploit misissued certificates to impersonate a trusted entity, such as a bank or an e-commerce website. Similarly, not monitoring certificate misuse can lead to suspicious activities such as the issuance of unexpected certificates. For example, without monitoring, an attacker could create unknown certificates to intercept all traffic on a domain causing a significant threat to data confidentiality and integrity.
These vulnerabilities underscore why legacy PKI systems are inadequate for securing modern digital environments. Therefore, PKI solutions with strong encryption, MFA, certificate pinning and real-time monitoring are critical to mitigate these risks and maintain a secure infrastructure.
Compliance Issues
Legacy PKI systems fail to meet modern compliance requirements like GDPR, HIPAA and PCI DSS due to outdated technologies, insufficient controls and a lack of good reporting mechanisms. These gaps can lead to non-compliance penalties, reputational damage and security vulnerabilities.
Let’s do a detailed analysis of how Legacy PKI systems struggle with each compliance standard.
General Data Protection Regulation (GDPR)
GDPR mandates the protection of personal data for individuals, requiring secure encryption, data access controls and timely breach reporting. Legacy PKI systems, which rely on outdated cryptographic algorithms (e.g., SHA-1 or RSA with small key sizes), cannot ensure secure encryption to protect personal data during transmission or storage. The lack of real-time monitoring in legacy PKI means organizations may not detect or respond to certificate misuse or data breaches in a timely manner, violating GDPR’s 72-hour breach notification rule.
Example: A healthcare organization using a legacy PKI might fail to secure patient records due to an expired certificate, exposing sensitive data to unauthorized access. This could result in massive fines under GDPR.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA requires organizations to handle healthcare data by implementing encryption, access controls and audit trails to protect patient information. Legacy PKI systems lack support for strong encryption protocols like TLS 1.3 and fail to provide proper logging or tracking of certificate activities. They may also rely on manual certificate management, increasing the risk of human errors, such as leaving certificates unrenewed, which can lead to data exposure.
Example: A hospital relying on a legacy PKI system for securing its communication might face a data breach if attackers exploit weak encryption or an expired certificate to access electronic health records, violating HIPAA requirements.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS mandates strong encryption and secure certificate management to protect cardholder data during payment processing. Legacy PKI systems struggle to meet these requirements because of their reliance on outdated encryption methods, lack of automation and poor visibility into the certificate lifecycle. Without features like automated renewal and revocation, expired certificates could expose payment systems to risks such as man-in-the-middle (MITM) attacks or unauthorized access.
Example: A retail company using a legacy PKI system for securing payment transactions might fail a PCI DSS audit if an expired SSL/TLS certificate exposes customer credit card data to attackers during a transaction.
Additional Challenges in Legacy PKI
Meeting New PKI Standards
Validation of evolving PKI best practices such as Key Rotation, Certificate Lifecycle management, strong authentication methods and certificate transparency is critical for both security and continuity of operations. However, industry standards, such as PCI DSS, SCEP, NIST and ISO, have heavy requirements that are challenging to manage. Even a single lapse, such as the expiration of a certificate, can cause considerable disruption, such as an application outage.
For example, in December 2021, a major outage at Spotify, Slack and AWS services was traced back to an expired certificate. The expiration disrupted services for millions of users, causing critical downtime for organizations relying on these platforms. Such incidents show the importance of automated PKI management processes to ensure that certificate renewals and deployments happen without errors or delays.
For many PKI teams, the management and enforcement of these standards appear to be an impossible task. Manual processes can lead to wasted hours and higher chances of making mistakes. Moreover, fragmented approaches to PKI management increase vulnerabilities, which only adds to the compliance challenge. A set of best practice frameworks and a proactive, structured approach are required to prevent and combat these risks.
Vulnerabilities in Legacy PKI Systems
Legacy PKI systems are inadequate to meet today’s security and operational requirements. They commonly fail to service modern business applications that demand security, scalability and convenience. Let’s consider that if legacy PKIs struggle to implement multi-factor authentication efficiently, the chances of falling victim to password-based attacks or other security breaches are higher.
In addition, there is an overall problem of lack of crypto agility in legacy systems. In cases of compromise of certificate authorities or where encryption algorithms become obsolete, you are required to quickly perform active batch replacement of the keys and certificates. However, legacy PKIs are typically ill-equipped to execute these replacements quickly, leaving organizations exposed to unnecessary risks.
Such vulnerabilities demonstrate the shortfalls of outdated PKI infrastructures and highlight the necessity of modern solutions that are agile, scalable and capable of being adopted to meet evolving security challenges effectively.
Inadequate PKI Expertise
Public Key Infrastructure (PKI) management is a specialized skill that is becoming both rare and expensive to acquire. Holding onto good IT and security talent is already a barrier for many organizations. Without the necessary expertise, teams are often forced to manage PKI systems alongside their primary responsibilities which not only drains valuable resources but also introduces substantial risks.
PKI mismanagement creates errors, misconfigurations and vulnerabilities that compromise an organization’s security. At worst, organizations wind up delegating PKI responsibilities to the wrong people, e.g., data entry staff, resulting in severe security failures. PKI systems are more prone to errors without trained professionals to help manage them, leading to further vulnerabilities that hurt both the organization’s security and efficiency.
To handle these challenges, organizations can invest in dedicated PKI training programs to upskill their internal teams with externally managed PKI service providers. Managed services ensure PKI systems are handled by experienced professionals by reducing the risk of errors while allowing internal teams to focus on their own responsibilities. This approach maintains security, streamlines operations and provides confidence in managing risks in a complex environment.
Outdated PKI Systems
Legacy PKI systems, which have an age of decades, are unable to keep pace with today’s fast-changing and complex business environment. As these systems are outdated, they are in need of urgent updates. As a result, failing to refresh aging PKI infrastructure can significantly impact organizational competitiveness and potential loss of revenue through prolonged downtime and system outages.
Current encryption methods could be easily breached or compromised in the post-quantum world. These obsolete systems make organizations susceptible to security breaches showing that organizations must prioritize on upgrading their PKI solutions to secure themselves and keep a competitive edge.
Financial Burden of Managing Legacy PKI
Keeping up with PKI still comes with a significant financial burden to organizations. Organizations must source and maintain equipment such as servers, hardware security modules (HSMs) and load balancers. The problem is that these resources need to be maintained, which adds an overhead cost. Moreover, deploying and configuring this infrastructure is a time-consuming and manual process that distracts valuable human and financial resources from other core business functions.
Legacy PKI infrastructure is also becoming a more expensive everyday solution due to the cumulative cost of maintaining it. Once organizations become larger and their needs become more complex, the financial and operational burden of managing outdated PKI systems can quickly outweigh the benefits, prompting the need for modernization or outsourcing.
Insufficient PKI Scalability
With organizations adopting new systems and practices such as microservices, containerization and DevOps over the coming years, the demand for secure machine-to-machine connectivity also increases. Unfortunately, legacy PKI systems do not scale well to support these requirements, making it difficult to extend authentication to cloud-native workloads. The fact that the current solution cannot scale means that the possibility of drift is increased, which comes at the cost of being able to deploy new applications and services.
The inability of legacy PKI to adapt to the complexities of modern IT infrastructures leads to delays in rolling out innovative projects. As a result, businesses may experience setbacks in their ability to stay competitive and maintain operational efficiency. This highlights the urgent need for scalable and modern PKI solutions that can keep up with evolving business needs and technology advancements.
Evolution of Public Key Infrastructure (PKI)
The evolution of Public Key Infrastructure (PKI) can be categorized into three main phases, each marked by specific use cases and technological advancements:
Internet PKI
Historically, organizations used PKI to secure their external-facing applications and websites in the early Internet days. Public Certificate Authorities (CAs) such as VeriSign (now DigiCert) and Comodo would provide SSL/TLS certificates to ensure trust. For example, e-commerce platforms like Amazon and eBay use these certificates to bypass specific threats such as man-in-the-middle (MITM) attacks and data interception ensuring that customer transactions and sensitive information like credit card details are transmitted securely.
While this approach helped mitigate critical security risks, the adoption of Internet PKI was limited due to several challenges. The high cost of obtaining certificates from a small pool of trusted CAs made it difficult for smaller organizations to implement strong security measures. The process of managing these certificates was manual and complex, lacking automation in tasks such as renewal and revocation. These challenges increased the risk of expired or misconfigured certificates, which could lead to security vulnerabilities.
Enterprise PKI
As organizations recognized the importance of securing internal networks and reducing their dependence on costly public CAs, the focus shifted toward implementing PKI internally. This transition allowed enterprises to address the limitations of Internet PKI by taking greater control of certificate issuance and management while meeting the growing demands of expanding networks.
As enterprise networks expanded, PKI was utilized internally to secure user authentication, network devices and access control systems. For example, organizations implemented PKI to manage Wi-Fi security with 802.1X authentication and to enable secure remote access through VPNs. Internal PKI setups, such as Microsoft’s Active Directory Certificate Services (AD CS), reduced dependency on public CAs and allowed enterprises to issue and manage their certificates, cutting costs significantly.
However, as the technology expanded with cloud computing, IoT devices and mobile technologies, enterprise PKI faced challenges in scalability, automation and integration with these emerging technologies.
Next-Generation PKI
The limitations of enterprise PKI, particularly in managing the dynamic demands of cloud environments, mobile technologies and IoT ecosystems, demanded a shift to modern, automated and scalable PKI solutions.
Modern PKI solutions are now integrated into ecosystems, such as AWS Certificate Manager for securing cloud services, Apple HomeKit for authenticating IoT devices and mobile device management (MDM) platforms to protect mobile endpoints. These advancements address the scalability and bridge the automation gaps of earlier PKI systems while introducing features with dynamic and interconnected ecosystems.
For example, electric vehicle manufacturers use PKI to authenticate charging stations and vehicles securely. The process is known as “Plug and Charge” which allows secure communication ensuring that only authorized vehicles can access charging services. The system operates by issuing unique digital certificates to both vehicles and charging stations, facilitating mutual authentication upon connection. This method not only enhances security but also simplifies the user experience by automating the authentication and billing processes.
Hidden Costs of Legacy PKI
It seems like the operational costs of legacy PKI are very effective, but when it comes to reality checks, some anticipated costs make it a poor choice for today’s generation.
Hardware Costs
In a legacy PKI, hardware plays a critical role in managing and securing cryptographic keys and digital certificates. Total hardware cost estimation is around $315K, which includes the cost of servers, load balancers, databases and HSMs to ensure redundancy and high availability.
If we split each hardware cost estimation, it comes out to be:
CA Servers: A large-scale PKI requires approximately 30 servers. These 30 servers include 10 production CA servers, 10 development CA servers and 10 backup and recovery servers. Each server costs around $3.5K, which results in a total of around $105K.
HSM Servers: Hardware Security Module (HSM) Server is a critical part of a PKI. It is a physical computing device that safeguards and manages secrets (most importantly, digital keys). A large-scale PKI requires around 4 HSM servers of $35K each, totaling around $140K.
Load Balancers: A load balancer is a device or service that distributes network traffic across multiple servers. A large-scale PKI requires at least 2 Load balancers. The estimated cost of each Load Balancer is around $20K, which makes a total of $40K for load balancers.
SQL Databases: To store the data, any firm would require a database and a large organization can depend just on 1 SQL server. About 4 SQL Servers are required in a large-scale PKI, which costs $15K per 2-core pack, making around $30K for four servers.
Resources Costs
As mentioned above, many servers and hardware modules are required in Legacy PKI, which directly or indirectly increases resource costs. This includes the cost of support and maintenance team. Approximately $372.5K is required to maintain your Legacy PKI properly.
Here is the breakdown of the total estimated Resource cost of Legacy PKI:
PKI Team: In organizations with large-scale legacy PKI systems, the PKI team plays a pivotal role in managing, maintaining and securing the infrastructure. Due to outdated technologies and manual processes, any organization would require a well-established PKI team to handle their complex PKI. The major resource cost in this sector is around $315K.
Rest of the Team: Legacy PKI is a bit more complex than modern PKI technologies and some other trained professionals are required to perform various minor tasks. The rest of the team includes the IT Administration, IT CA Administration and IT Integration.
- The IT Administration includes the members responsible for the overall health and operations of the IT infrastructure, including PKI components. The estimated cost of the IT Administration team is nearly $12.5K.
- The IT CA Administration team manages Certificate Authorities (CAs) and their associated components within the legacy PKI. The IT CA Administration team’s estimated cost is about $20K.
- The IT Integration team ensures that the legacy PKI system works seamlessly with other systems, such as cloud environments and IoT platforms. The estimated cost of the IT integration team is nearly $25K.
As mentioned, a long list of hidden charges in a Legacy PKI goes unnoticed most of the time. These hidden costs make the modern PKI solutions far better than the Legacy PKI.
Why are Modern PKI solutions better than Legacy PKI?
Modern PKI solutions have evolved to solve the limitations and challenges posed by legacy systems. While legacy PKI often relies on manual processes, outdated technology and limited scalability, modern solutions leverage features such as automation, scalability, security and cost-effectiveness to meet the demands of the organization. With organizations managing an increasing number of certificates, users and devices, modern PKI provides the flexibility, efficiency and better user experience needed to ensure seamless and secure operations, making it far superior to traditional approaches.
Here are some major features of modern PKI that make it far more beneficial than legacy PKI.
Automation
One of the standout features of modern PKI solutions is automation, which significantly improves efficiency and reduces the risk of human error compared to legacy PKI systems. In Legacy PKI, certificate lifecycle management, including issuance, renewal, revocation and replacement, often involves manual processes. These tasks require constant oversight from IT teams leading to wasted time, increased operational costs and a higher chance of misconfigurations or expired certificates.
Modern PKI solutions, on the other hand, automate these processes, ensuring certificates are managed seamlessly and without human intervention. For example, modern PKI platforms can automatically detect expiring certificates and renew them before they lapse, avoiding service disruptions.
Example: In 2021, Microsoft Teams suffered a temporary outage due to an expired SSL certificate, highlighting the risks of manual certificate management. A modern PKI solution with automation would have detected the approaching expiration, renewed the certificate and updated it in the system without requiring manual input. This capability not only ensures uninterrupted service but also frees up IT resources to focus on higher-priority tasks.
Scalability
Modern PKI solutions excel in scalability, addressing the limitations of legacy PKI systems when managing a growing number of users, devices and applications. Legacy PKI systems are often built with static architectures and manual processes that struggle to adapt to the dynamic needs of modern enterprises. As organizations expand, legacy systems can become overburdened, leading to delays, errors and higher operational costs.
In contrast, modern PKI solutions are designed to scale seamlessly with organizational growth. They leverage cloud-based infrastructure and dynamic provisioning, enabling organizations to handle large volumes of certificates across diverse environments, including IoT devices, remote workforces and hybrid IT systems. This flexibility ensures that certificate issuance, renewal and management remain efficient, even as the number of endpoints increases exponentially.
Example: Consider a large organization deploying thousands of IoT devices across multiple regions. A legacy PKI system would struggle to handle this scale due to its feature of manual certificate provisioning and its inability to integrate with modern IoT platforms. In contrast, a modern PKI solution can automatically manage certificates for all devices in real-time by using APIs and cloud-native technologies. This ensures secure communication between devices without operational bottlenecks even if the deployment scales into the millions.
Security
Modern PKI solutions provide enhanced security features that address the gaps and vulnerabilities often found in legacy PKI systems. Legacy PKI systems were designed for simpler environments and lacked the advanced security mechanisms required to protect against modern threats such as cyberattacks, phishing and key compromise. Additionally, legacy systems often depend on manual processes, which increase the chance of human error, misconfigurations and delayed responses to security incidents.
Modern PKI solutions, on the other hand, incorporate strong security measures such as hardware security modules (HSMs), certificate transparency logs, automated key rotation and secure certificate storage. They also use advanced encryption algorithms such as Elliptic Curve Cryptography (ECC), SHA-256 and SHA-3, RSA with longer key lengths (2048-bit or 3072-bit) and emerging Post-Quantum Cryptography (PQC) algorithms and integrate seamlessly with modern security tools like SIEM (Security Information and Event Management) systems to detect and respond to threats in real-time. These features ensure that certificates are not only managed securely but also meet compliance standards for evolving regulatory requirements.
Example: In 2019, the massive Capital One data breach exposed sensitive customer data due to the misuse of compromised credentials. With a modern PKI solution, organizations can implement stronger authentication mechanisms, such as certificate-based authentication, which eliminates reliance on passwords and prevents such breaches. Additionally, automated certificate revocation and renewal features in modern PKI would have enabled Capital One to mitigate risks associated with compromised keys quickly.
Cost-Effectiveness
Modern PKI solutions are more cost-effective than legacy systems due to their automation, cloud-based infrastructure and streamlined management processes. Legacy PKI systems often require high investments in hardware, manual processes for certificate management and expensive infrastructure maintenance. As organizations scale, these costs increase and managing a large number of certificates becomes more difficult, leading to inefficiencies.
In contrast, modern PKI solutions reduce operational costs by automating tasks such as certificate issuance, renewal and revocation. Cloud-based solutions eliminate the need for costly on-premises infrastructure, while advanced security features help minimize the risk of breaches and reduce the costs related to security incidents.
Example: Consider a company that has been using a legacy PKI system to manage certificates for its internal network and multiple web applications. The organization must employ an entire team to manually manage the certificates, perform renewals and troubleshoot issues. As the organization grows and the number of certificates increases, the costs associated with maintaining the legacy system rise exponentially.
By switching to a modern, cloud-based PKI solution, the company can automate most of these tasks, reducing the need for manual intervention and lowering labor costs. The cloud solution also offers scalability; therefore, the company doesn’t need to invest in expensive infrastructure as it expands.
User Experience
Modern PKI solutions provide a much better user experience than legacy systems primarily due to their user-friendly interfaces and smooth integrations with other systems. Legacy PKI systems involve complex manual processes and require users to navigate through multiple outdated tools, making tasks such as certificate management and renewal difficult and prone to errors.
In contrast, modern PKI solutions offer user-friendly dashboards, simplified workflows and automation that increases user experience. They integrate easily with other systems and services, allowing users to manage certificates, renewals and security systems in a centralized and user-friendly environment. Additionally, modern PKI platforms often provide self-service portals for end-users to manage their certificates, reducing the burden on IT teams and improving overall efficiency.
Example: A financial institution using a legacy PKI solution may require its employees to manually request certificates and go through several approval stages and wait for IT to install and configure them. This process is slow, error-prone and frustrating for users. In contrast, with a modern PKI solution, employees can use a self-service portal to request, renew and install their certificates with minimal involvement from IT. The system automatically handles approval workflows, reducing waiting times and improving productivity.
How does Encryption Consulting help?
Encryption Consulting comes with a solution of PKIaaS (PKI – as – a – Service). We offer you a customizable and high-assurance PKI that is built to the highest standards. It is a low-risk managed solution that provides you with full control of your PKI without worrying about the complexity.
Encryption Consulting offers a comprehensive Certificate Lifecycle Management solution, CertSecure Manager. From certificate discovery and inventory management to issuance, deployment, renewal, revocation and reporting, CertSecure delivers a complete solution. With features like intelligent report generation, automated alerts, seamless deployment to servers and certificate enrollment, CertSecure enhances efficiency and sophistication, making it a powerful and adaptable tool for managing certificates.
Encryption Consulting’s PKI advisory services simplify the complexities of your PKI. We bring our expertise in designing, implementing, managing and migrating PKI systems and providing consulting to organizations in various industries such as banking, manufacturing, retail, energy, health and life science.
Conclusion
Legacy PKI systems were the foundation of cybersecurity in the past, but the hidden costs made them less popular among cybersecurity specialists. From high hardware and resources expenses to inefficiencies in security, scalability, automation and integration, legacy PKI becomes a financial and operational burden for the organization.
On the other hand, modern PKI systems and solutions seem more cost-efficient and achievable. It provides high-security measures with modern and efficient encryption and hashing algorithms like RSA with SHA-2 (SHA-256 or SHA-384). With Encryption Consulting’s PKIaaS and advisory solutions, you can easily migrate your legacy PKI to a strong, scalable and secure PKI that will fulfill your organization’s security needs.