Everyone wants to keep themselves secure and to do so, people spend a vast amount of fortune. Therefore, security investment has increased significantly in the past few decades, and various new technologies and techniques have been discovered to tackle security leaks. Yet human mistakes are often overlooked among them. There isn’t a single person alive who has never made mistakes; making mistakes is a fundamental part of human nature – that’s how humans grow and learn.
An attacker can use many high-level vulnerabilities to break into a system. According to a study by IBM, human mistakes are the leading cause of 95% of cyber security breaches. Data loss, misdelivery, and other human-related errors were listed among them. So, if we somehow eliminate these errors, 9.5 out of 10 cyber breaches may not have occurred.
Still, in many cases, the attacker’s success involves provoking or capitalizing on human error, like using social engineering to guess the password or something similar.
Social Engineering
Social Engineering is a term related to a broad range of human interaction attacks. It mainly uses psychological manipulation to trick users into making security mistakes like concealing their true identities and motives by presenting themselves as trusted individuals. It is quite a popular technique among attackers as it’s often easier to exploit people than any network or software.The first step in social engineering attacks is gathering information or performing research on the target. Target may be an enterprise, so in that case, the attacker will gather information regarding the organizational structure, internal operations, employees, and so on. One common tactic is to focus on the behavioral patterns of employees who have initial access by scanning their social media profiles or behavior online. There are various types of social engineering techniques. A few of the most common types are:
- Baiting
As the name suggests, in this type of attack, an attacker uses the greed or curiosity of the user. Suppose an attacker leaves a malware-infected external device in a place that is sure to be found by an innocent user. The user, or in this case, “target”, inserts this device into their system and unintentionally installs the malware.
- Pretexting
Pretexting involves an attacker obtaining information through a series of lies or scams to gain access to the confidential data of the target (user). A pretexting fraud could involve an attacker pretending to need financial or personal data to verify whether the user is authenticated or not. This way, the attacker will gain data from the user.
- Scareware
This technique involves the user believing that their system is infected with malware, to which an attacker offers a solution. This, in reality, is a trick to gain access to the user’s system utilizing providing solution.
- Diversion Theft
This involves tricking a delivery agency into going to the wrong pickup or drop-off address and intercepting the transaction. An agency can carefully avoid this if they are more careful about things.
- Quid pro quo
In this type of attack, an attacker pretends to provide something to the target in exchange for some information. For example, an attacker may call a target (randomly selected) pretending to be technical support. This way, the attacker may come across some genuine user who needs help and have them launch some malware or gather information from them by interaction.
In 2013, the Syrian Electronic Army was able to gain access to the Associated Press’ Twitter account by a phishing email, which contained a malicious email. An Attacker sent this email to an AP employee under the guise of another fellow employee. This way, the hacker could send fake news from AP’s Twitter handle. AP could have prevented these if the technology department had carried out routine checks on employees and had a secure email gateway.
What does Human Error mean in Cyber Security?
Human error means unintentional actions like an email misdelivery (email sent to wrong recipient or address) or poor password hygiene (weak passwords are relatively easier to crack or guess) by the employees or users that cause, spread, or allow a security breach. So, this contains a vast range of activities, from downloading a virus-infected application to failing to use a strong password. These are a few reasons why human error is so challenging to address. With so many websites, tools, and services used, employees and users need different usernames and passwords, making them opt for shortcuts to make life a bit easier. This increases the threat of cybercriminal activities and other types of security breaches.
Why is Human Error so Dangerous?
Security breaches exploit the weakest link, which in many cases are humans themselves than any of the code they write. These human errors can be exhibited in multiple ways – from failing to stop a phishing attack (clicking an anonymous source’s link and exposing the network to the attacker) to having weak passwords. It also leads to Data breaches.
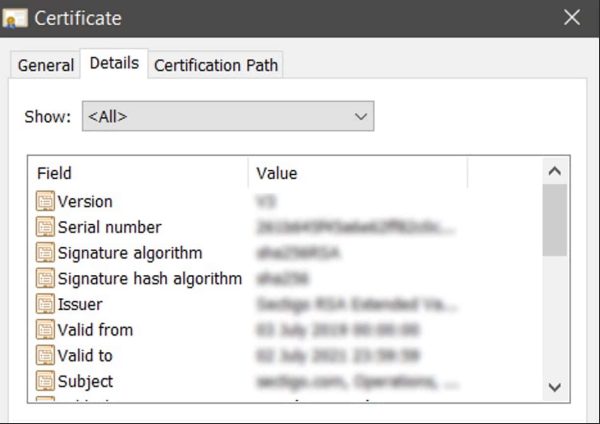
A cybercriminal can manage to guess the password or use social engineering to get an employee to make some payment to a transaction site controlled by the criminal, if proper technical security measures are not taken care of (SSL Cert or good firewall).
What factors lead to Human error?
Several factors play into human error, but the most common are these three-
- Opportunity
Error can occur when there is an opportunity for it. This process may seem apparent initially, but if more options are there for things to go wrong, the chances are that users may make a mistake.
- Lack of awareness
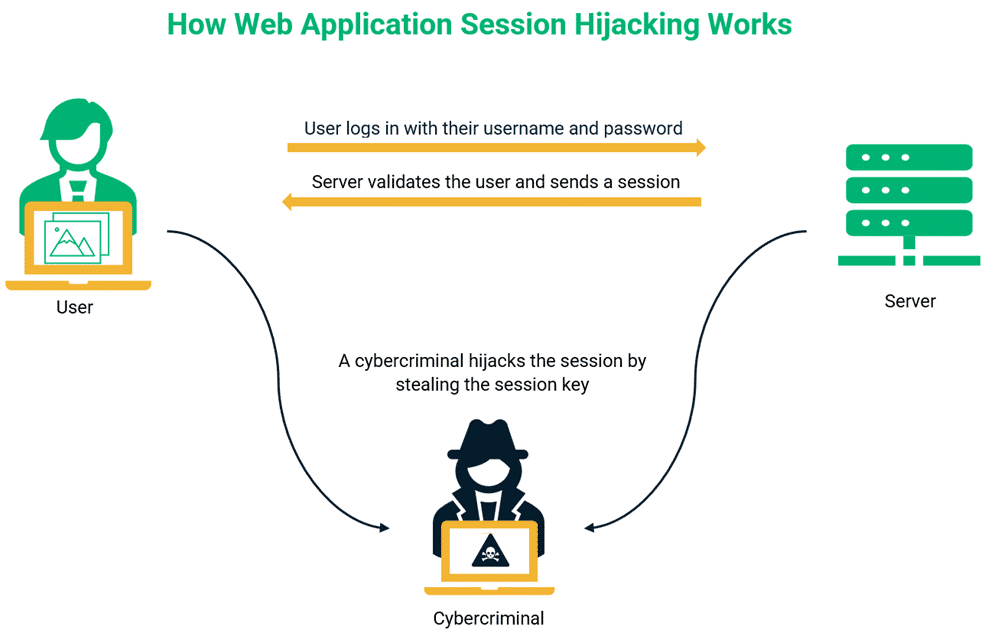
Most human errors result from users not knowing the right course of action. For example, users who aren’t aware of the risk of phishing are far more vulnerable to falling for phishing attacks, and someone who doesn’t know the risk of public Wi-Fi will quickly have their session hijacked or credentials stolen.
- Environment
There are many environmental factors leading to human errors. The physical environment of a workplace can increase the number of mistakes. Culture also plays an important role here. An end-user will often know the right course of action, but they may fail to carry it out because there may be an easier way to do things or believe it is not essential. A culture where security is always left in the background will lead to more errors.
Few examples of Human Error
Human error can compromise security in endless possible ways, but some types of error stand out more than others.
- Misdelivery
Sending some information to the wrong recipient is a pervasive threat to data security. One of the most severe data breaches was caused when an NHS practice revealed the email addresses (identity) of more than 800 patients who had visited HIV clinics. The employee sending those emails to HIV patients accidentally entered their email address into the “To” field rather than the “Bcc” field.
- Patching
Cyber attackers are constantly looking for new exploits in the software technologies. So, when these exploits are discovered, the developers resolve them and send out the patch or updates to all the users before cybercriminals can attack. That is why it is essential to install the security updates at the earliest. In 2017, WannaCry ransomware affected many computers worldwide, damaging millions of dollars. Yet the exploit, dubbed ‘EternalBlue’, was patched by Microsoft months before the attacks.
- Password problems
This saying – “Humans and passwords simply don’t get along,” may be funny, but it’s valid to a certain extent. The National Centre for Cyber Security’s 2019 report showed an unfortunate truth, 123456 remains the most popular password globally, and 45% of people reuse the password of their primary email account on other services.
- Phishing attack
Sometimes, attackers might leave an external drive (like a USB drive) within the user’s or target’s reach. The user or target could connect this external drive to their system out of curiosity. And in this way, the attacker would be able to carry out a successful phishing attack. Thus, the user needs to be careful and think more than once before performing such actions.
Types of Human Error
There are many chances and situations for human errors. Still, people can broadly categorize them into two different types. Their difference is whether the user or person in question has the necessary knowledge to perform the correct action.
- Skill-based error
These consists of small mistakes like slips and lapses while performing familiar tasks and activities. These may occur when an employee or a user is tired or not paying attention, is distracted, etc. Here, the end-user knows the correct approach but fails to do so by error or negligence.
- Decision-based error
These errors arise when a user makes a wrong decision, which may occur in either of the scenarios – the user not having required knowledge, not having enough information, or not realizing that they are leading to a decision from their action.
How do we prevent Human errors?
By applying the following practices and solutions, there’s a chance to prevent security breaches effectively:
- Update corporate security policy
An organization’s security policy should clearly outline how to handle critical data (including passwords, too), who can access those, and what security software to use upon these data.
- Use the principle of least privilege
The most straightforward way to secure data access is to deny all access by default. Using Zero Trust security or network to design an IT system is a very secure approach where users and employees of an organization are authenticated, authorized, or continuously validated for security purposes. Privileged access can however be granted on a case basis. This way, organizations can prevent accidental data leaks.
- Offer regular training and personal development
Technology is in a state of constant advancement, so demands from clients and customers are also increasing. Training and opportunities to acquire new skills can help employees keep themselves up-to-date.
- Consider cloud storage and document management
Using the cloud to store the documents means that the files are backed up regularly, and more than one individual has access.
Conclusion
Humans don’t have to be the weakest link, though. The fewer opportunities for mistakes, the fewer users are tested for their knowledge; the more knowledge users possess, the less likely they are to make mistakes. Statistics show that 95% of security breaches are due to human error. Still, it also shows that even the smallest step towards resolving human error can end up being the biggest one in ensuring robust security.